28-12
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 28 Group Encrypted Transport (GET) VPNs
Configuring GET VPN
GET VPN uses the Synchronous Anti-Replay (SAR) mechanism to provide anti-replay protection for
multisender traffic. SAR is independent of real-world Network Time Protocol (NTP) clock or
sequential-counter mechanisms (which guarantee packets are received and processed in order). A SAR
clock advances regularly. The time tracked by this clock is called pseudotime. The pseudotime is
maintained on the key server and is sent periodically to the group members within a rekey message as a
timestamp field called pseudoTimeStamp. Group members have to be resynchronized to the pseudotime
of the key server periodically. The pseudotime of the key server starts ticking from when the first group
member registers. Initially, the key server sends the current pseudotime value of the key server and
window size to group members during the registration process. New attributes, such as time-based
replay-enabled information, window size, and the pseudotime of the key server, is sent under the SA
payload (TEK).
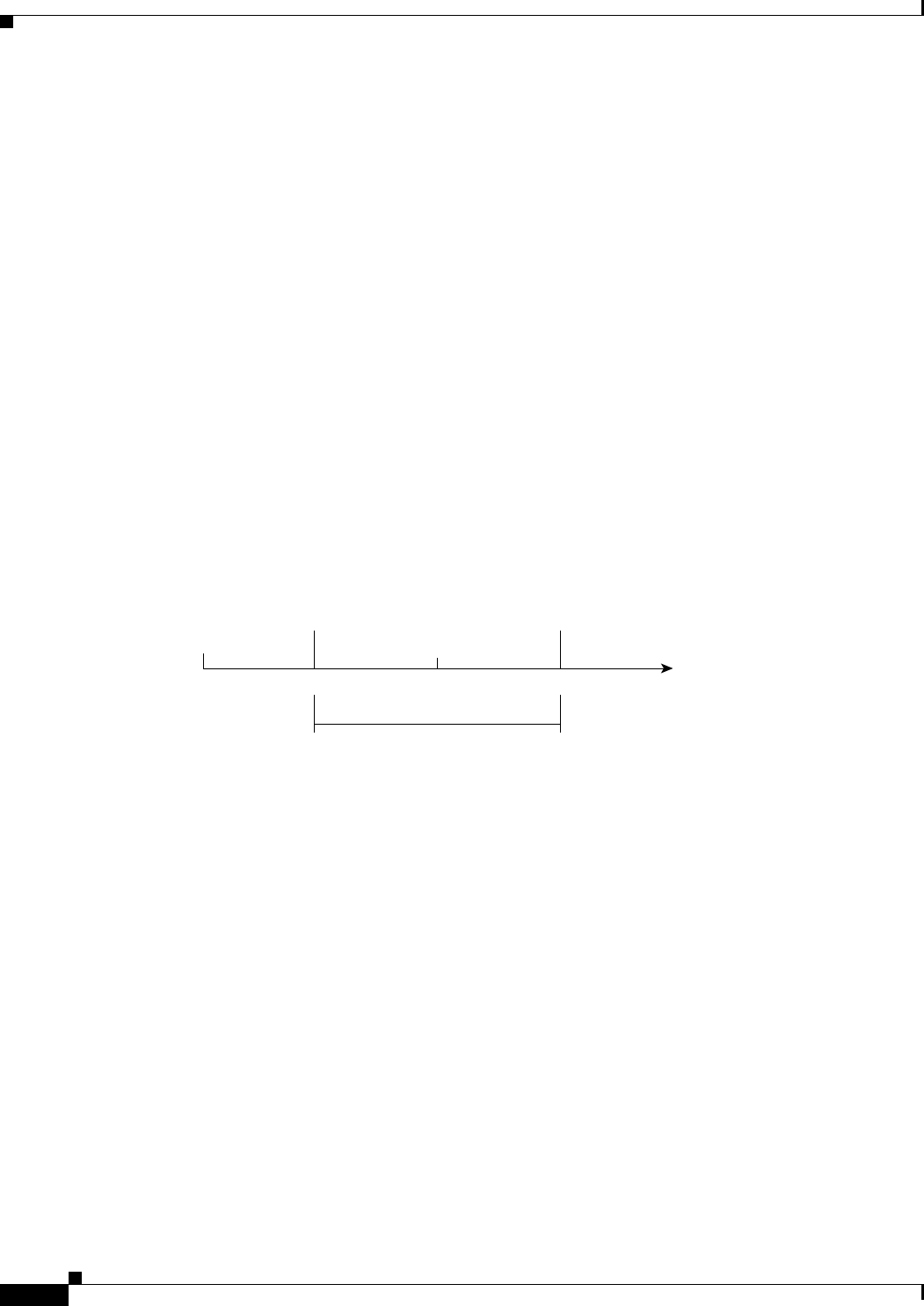
The group members use the pseudotime to prevent replay as follows: the pseudoTimeStamp contains the
pseudotime value at which a sender created a packet. A receiver compares the pseudotime value of
senders with its own pseudotime value to determine whether a packet is a replayed packet. The receiver
uses a time-based anti-replay window to accept packets that contain a timestamp value within that
window. The window size is configured on the key server and is sent to all group members.
The following figure illustrates an anti-replay window in which the value PTr denotes the local
pseudotime of the receiver, and W is the window size.
You configure anti-replay in the security association definitions in the Group Encryption Policy. For
more information, see Defining GET VPN Group Encryption, page 24-51 and Add New or Edit Security
Association Dialog Box, page 24-55.
Figure 28-3 Anti-Replay Window
Configuring GET VPN
To configure a full mesh VPN with group encrypted transport (GET), use the Create VPN wizard as
described in Creating or Editing VPN Topologies, page 24-28. When you finish the wizard, you are
asked if you want to synchronize RSA keys, which is required for normal VPN functioning; for detailed
information, see Generating and Synchronizing RSA Keys, page 28-13.
If you select multicast as the rekey transport mechanism, you must enable multicast on all key servers
and the desired group members. For more information, see Choosing the Rekey Transport Mechanism,
page 28-6.
You can change only the name and description of a GET VPN using the Edit VPN wizard. If you need
to make changes to other policies and settings, open the policies from the Site-to-Site Manager page, as
follows:
• For ISAKMP and IPSec settings, select Global Settings for GET VPN. See Configuring Global
Settings for GET VPN, page 28-16.
• For IKE proposal policies, select IKE Proposal Policy for GET VPN. See Configuring the IKE
Proposal for GET VPN, page 28-15.
Reject
Initial
pseudotime
PTr - W PTr
Anti-replay window
PTr + W
Accept Reject
230078


















