30-57
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 30 Managing Remote Access VPNs on ASA and PIX 7.0+ Devices
Working with SSL and IKEv2 IPSec VPN Policies
To configure the ASA to allow KCD, once the ASA joins the domain, an entry should appear under
the Users and Computers list on the domain controller for the ASA. In the Properties dialog box, on
the Delegation tab, select Trust this computer for delegation to specified services only, and then
select Use any authentication protocol. In the table of authorized services, add all services for
which the ASA is delegated for authentication on behalf of users.
Tip For definitive information on configuring this feature on the Windows domain controller, refer to the
Microsoft documentation.
For the ASA to use Kerberos constrained delegation, you must configure the ASA as described in
Configuring Kerberos Constrained Delegation (KCD) for SSL VPN (ASA), page 30-58. The feature is
available on ASA Software release 8.4 and higher only.
Following is an example that explains how Kerberos constrained delegation works with a clientless SSL
VPN hosted on an ASA.
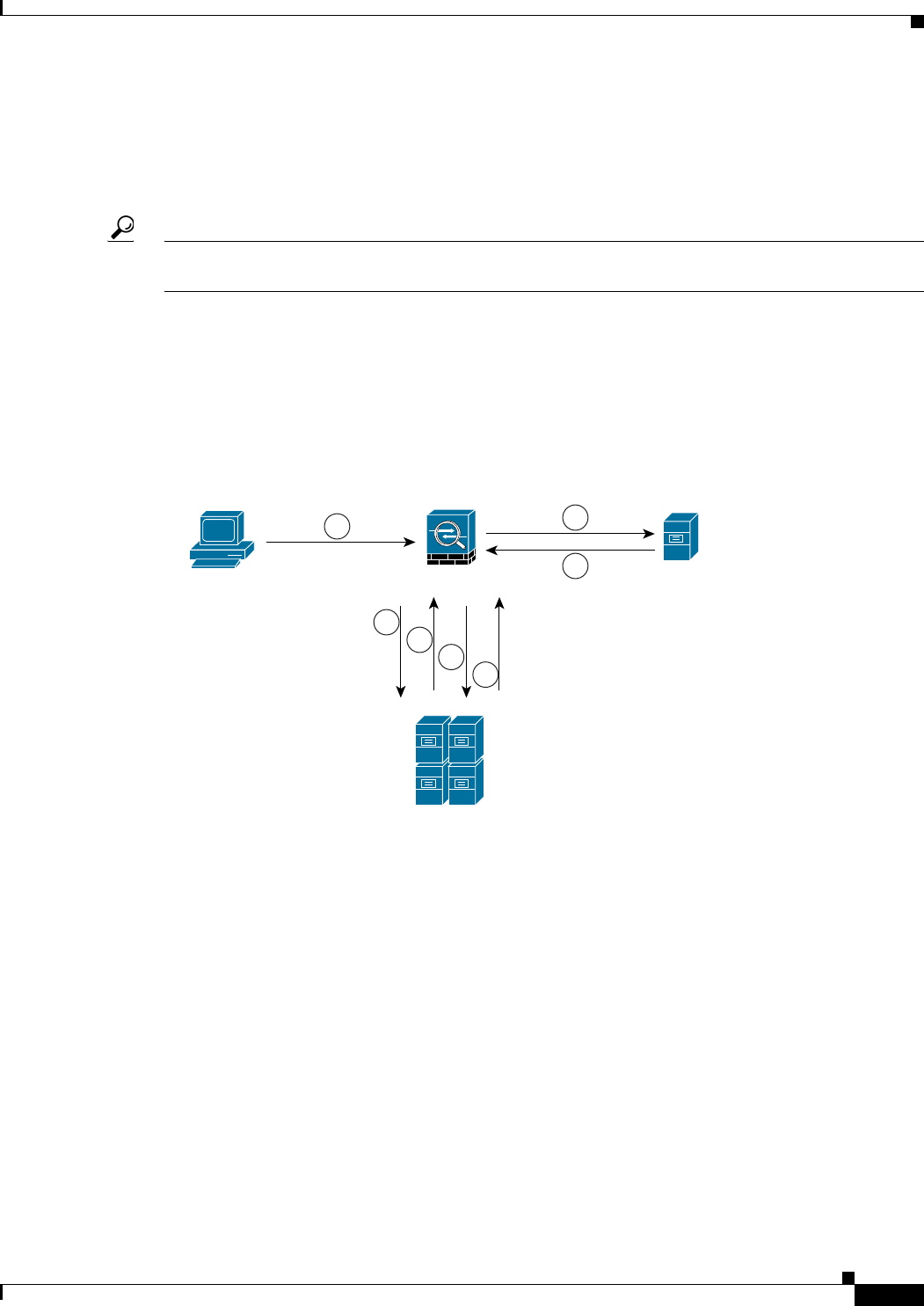
Figure 30-1 Kerberos Constrained Delegation Example
After verifying the identity of an SSL VPN user with the configured authentication mechanism, the ASA
uses protocol transition to switch to the Kerberos protocol for authentication on behalf of the user and
then sends a Kerberos service ticket instead of the user’s credentials to a published Web server that
accepts Kerberos for authentication. Following are the steps:
1. An SSL VPN user session is authenticated by the ASA using the authentication mechanism
configured for the user. For example, in case of Smartcard credentials, the ASA extracts the required
information (the user’s principle name) from the digital certificate and performs LDAP
authorization against Windows Active Directory.
2. After successful authentication, the user logs into the ASA SSL VPN portal page. The VPN user
accesses a web service by entering a URL in the portal page or by clicking on a bookmark. If the
access requires authentication, the server challenges the ASA for credentials and along with the
challenge sends a list of authentication mechanisms supported by the server. Based on the HTTP
headers in the challenge, the ASA deduces whether the server requires Kerberos authentication. If
connecting to a backend server requires Kerberos authentication, then the ASA requests an
impersonate ticket, for itself on behalf the user, from the KDC.
1
6
7
2
3
4
5
ASA
236624
Clientless
SSL VPN user
Kerberized
server
Domain Controller (KDC)


















