40-10
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 40 Managing IPS Anomaly Detection
Configuring Anomaly Detection
During learning mode, anomaly detection develops histograms for each TCP and UDP port, and for other
protocols, to create a baseline of the normal behavior of your network (see Anomaly Detection Modes,
page 40-2). For example, the histogram for a TCP port lists the “normal” number of source addresses
that make incomplete connections to a certain number of destination addresses during a minute. The
histograms contain three buckets: low number of destination addresses (5), medium number (20), and
high number (100). (The destination buckets are a fixed number.) Separate histograms are kept for each
service and zone (see Anomaly Detection Zones, page 40-3).
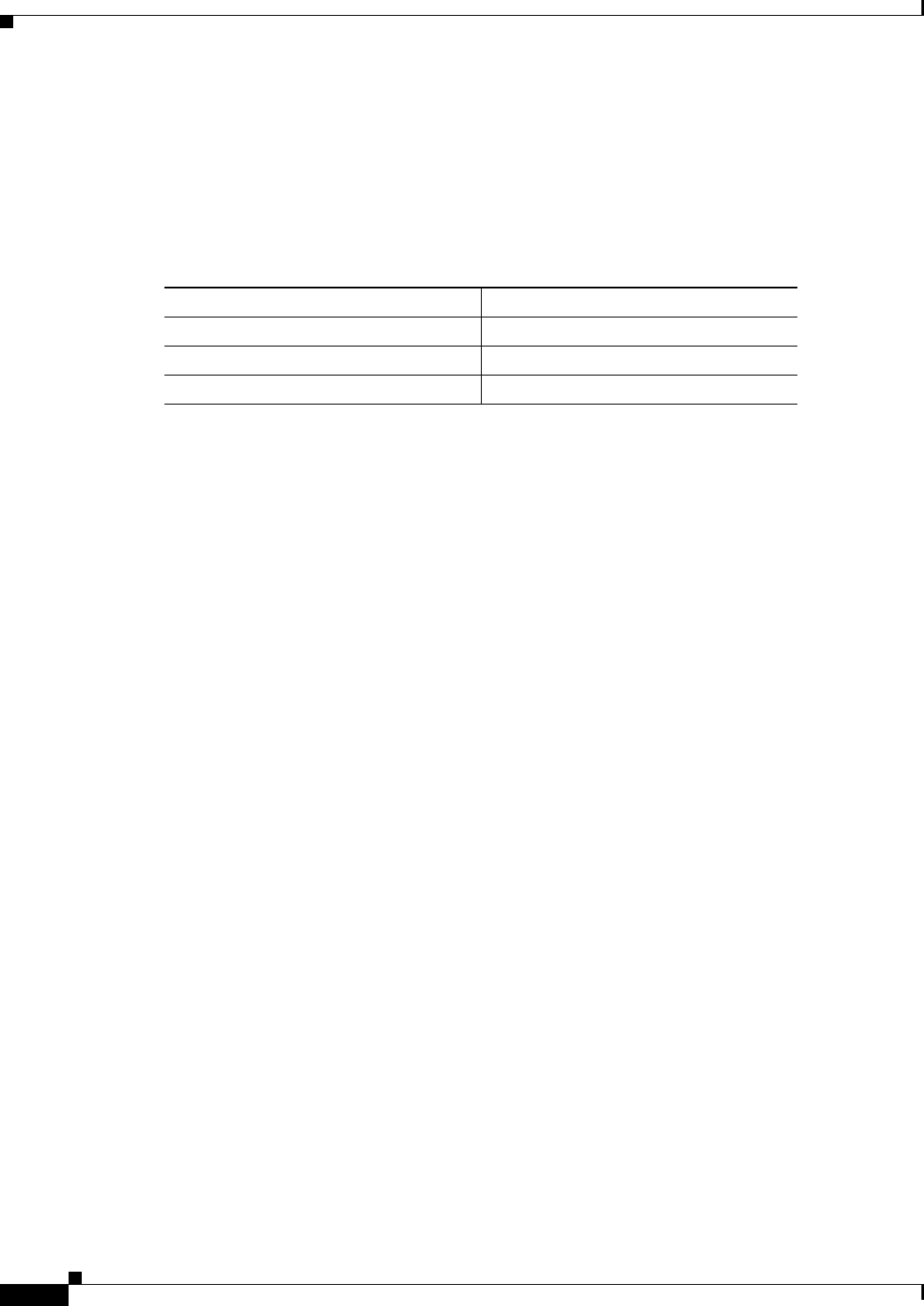
For example, learning mode might develop the following histogram for TCP port 80:
In addition to these learned histograms, the anomaly detection scanner has a threshold setting that you
configure. You configure a general scanner threshold, and you can override the threshold (configuring a
different value) for any specific service (TCP port, UDP port, or other protocol). Each zone has its own
thresholds.
When anomaly detection moves to detect mode, where it is actively scanning for worms, the thresholds
and histograms are used as follows:
• Histograms are ignored until the threshold for the service is exceeded. For example, consider the
above table for TCP/80 traffic. If the threshold is set at 200 (the default), a scanner must scan 200
hosts in a minute to trigger a scanner alert. If 7 source addresses scanned 50 hosts (which is an
anomaly in the histogram, which expects no more than 6 hosts scanning 20-99 destinations), but a
single scanner scanned only 100 addresses, no alert is generated, and no anomaly is detected.
• When the scanner threshold is exceeded, anomaly detection uses the histogram to determine if the
service is under worm attack. In this example, if a source scans more than 200 destinations, anomaly
detection evaluates the collected activity in the network. Because 7 hosts have scanned 50 hosts, a
worm alert is generated.
When under worm attack, anomaly detection stops learning and clears the current learning
information. It also temporarily lowers the thresholds.
• When a worm attack is detected, the worm timeout counter is started. When the timeout is reached,
the scanner is reset. If the worm attack continues, new alerts are generated. You configure the worm
timeout on the Operation Settings tab of the Anomaly Detection policy.
If you leave the defaults in place, anomaly detection generates histograms based on what it learns about
your network from the network’s actual behavior. However, if you understand your network you can
fine-tune these histograms to reduce false positives, creating your own definition of expected (or desired
or tolerated) behavior for each TCP/UDP port or other protocol, for each zone. You can create your own
histograms for only those services that interest you, and leave the defaults for all other ports.
Additionally, you can configure the general scanner threshold for each zone, and configure different
thresholds for specific services.
For information on configuring thresholds and histograms, see Configuring Anomaly Detection
Thresholds and Histograms, page 40-11.
Number of Destination Addresses Number of Source Addresses
Low (5) 18
Medium (20) 6
High (100) 2


















