56-15
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 56 Configuring Service Policy Rules on Firewall Devices
IPS, QoS, and Connection Rules Page
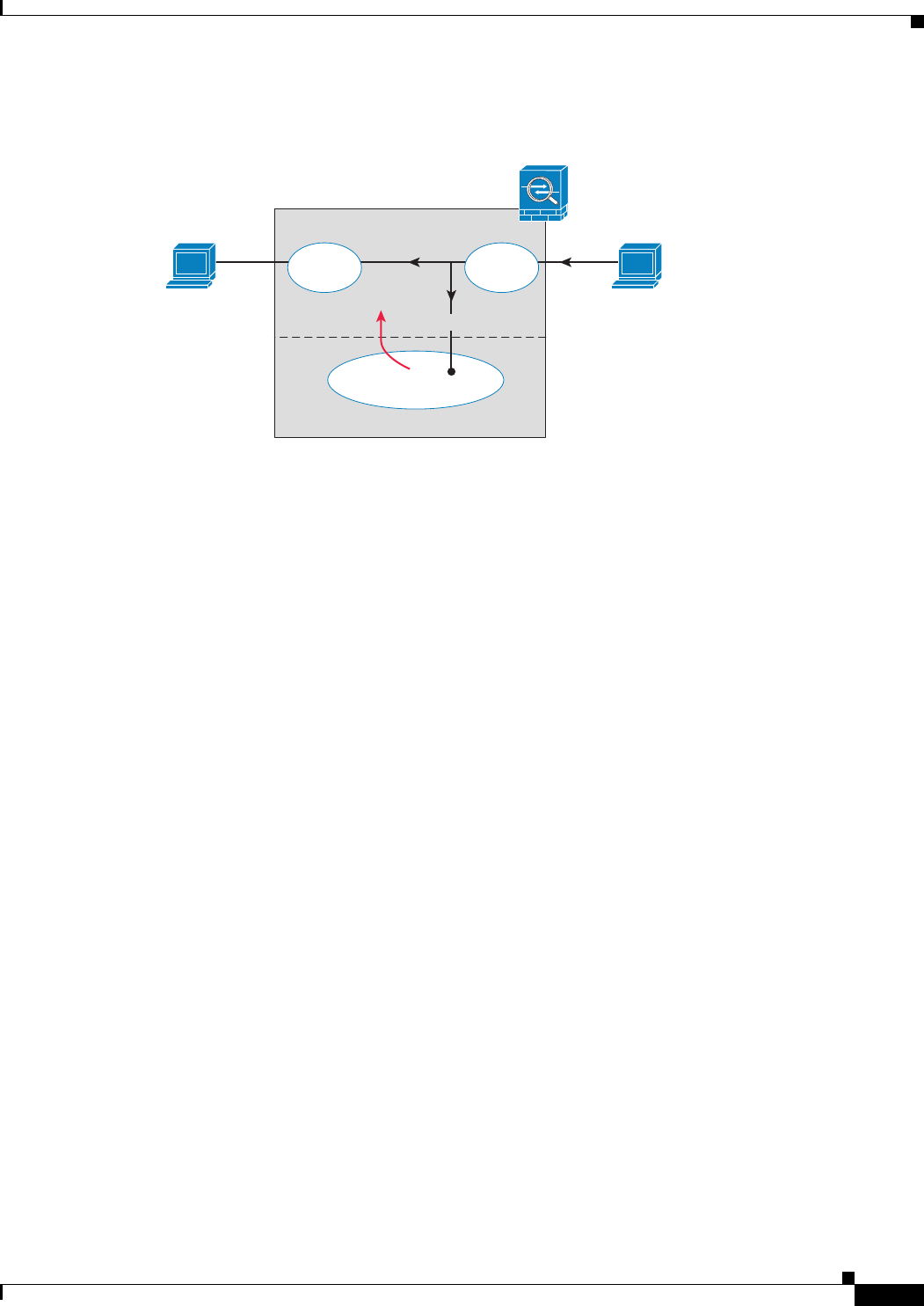
The next illustration depicts traffic flow when the IPS module is running in Promiscuous mode. In this
example, the IPS module sends a shun message to the ASA for traffic it has identified as a threat.
Related Topics
• Adding Devices to the Device Inventory, page 3-6
About the ASA CX
The ASA CX is a Security Services Processor (SSP) that can be installed in the Cisco ASA-5585-X
series Adaptive Security Appliance. You configure the parent ASA to redirect traffic to the ASA CX,
which then applies its security policies and either drops the traffic, or returns it to the ASA for further
processing and routing to the next destination.
There are two basic policies that may need adjustment in the ASA when you add a ASA CX: access rules
and inspection rules:
• Access rules, whether global rules or those applied to specific interfaces, are always applied before
traffic is redirected to the ASA CX. Thus, the security card sees only the traffic already permitted,
and does not process traffic that was dropped at entry to the ASA. Consider adjusting the rules to
ensure that all traffic that you want the ASA CX to process is permitted.
• Inspection rules determine which traffic is inspected. The ASA CX does not inspect traffic that has
already been inspected by the ASA. Therefore, you must ensure that you do not inspect traffic that
you intend the ASA CX to inspect. Specifically, do not inspect HTTP traffic, because HTTP
inspection is one of the core functions of the ASA CX. The default inspection rules on the ASA do
not include HTTP inspection, so you must alter your inspection rules only if you added HTTP rules.
Determine if you need to create access rules for an interface, or global access rules that apply to all
interfaces. Use the ASA access rules to filter traffic before it is redirected to the ASA CX. If you know
there are classes of traffic that you never want to pass, it is more efficient to drop them immediately upon
entry to the ASA.
If you have already established access rules, there is no requirement to change them. However, you
should evaluate whether they need to be relaxed in order to have the ASA CX process certain types of
traffic that you are now dropping by means of access rules.
Enabling traffic redirection to an installed ASA CX is described in Step 3. Configure the MPC actions,
page 56-8 of the Insert/Edit Service Policy (MPC) Rule Wizard, page 56-6.
Security Appliance
Main System
inside
AIP module or card
IPS inspection
outside
Backplane
VPN
Policy
Firewall
Policy
Shun
message
199662
Copied Traffic


















