5-5
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 5 Managing Policies
Understanding Policies
Rule Order When Using Inheritance
As described in Understanding Access Rules, page 16-1, an access list (ACL) consists of rules (also
called access control entries or ACEs) arranged in a table. An incoming packet is compared against the
first rule in the ACL. If the packet matches the rule, the packet is permitted or denied, depending on the
rule. If the packet does not match, the packet is compared against the next rule in the table and so forth,
until a matching rule is found and executed.
This first-match system means that the order of rules in the table is of critical importance. When you
create a shared access rule policy, Security Manager divides the rules table into multiple sections,
Mandatory and Default. The Mandatory section contains rules that cannot be overridden by the local
rules defined in a child policy. The Default section contains rules that can be overridden by local rules.
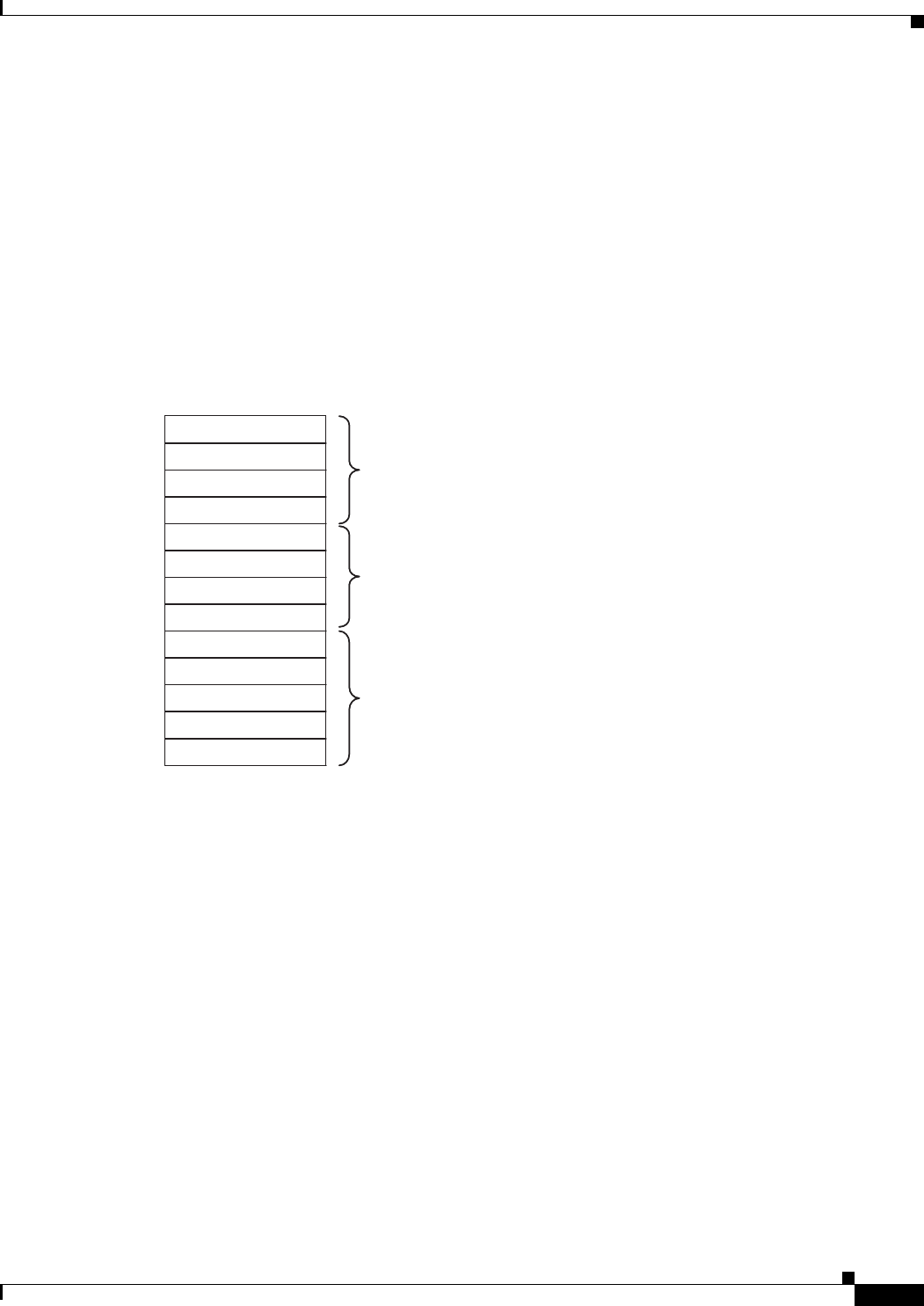
Figure 5-2 describes how rules are ordered in the rules table when using inheritance.
Figure 5-2 Order of Rules When Using Inheritance
Benefits of Using Inheritance
The ability to define rule-based policies in a hierarchical manner gives you great flexibility when
defining your rule sets, and the hierarchy can extend as many levels as required. For example, you can
define an access rule policy for the device at a branch office that inherits rules from a parent policy that
determines access at the regional level. This policy, in turn, can inherit rules from a global access rules
policy at the top of the hierarchy that sets rules at the corporate level.
In this example, the rules are ordered in the rules table as follows:
Mandatory corporate access rules
Mandatory regional access rules
Local rules on branch device
Default regional access rules
Default corporate access rules
The policy defined on the branch device is a child of the regional policy and a grandchild of the corporate
policy. Structuring inheritance in this manner enables you to define mandatory rules at the corporate
level that apply to all devices and that cannot be overridden by rules at a lower level in the hierarchy. At
the same time, rule inheritance provides the flexibility to add local rules for specific devices where
needed.
Mandatory ACE-1
Mandatory ACE-2
Mandatory ACE-n
Local ACE-1
Local ACE-2
Local ACE-n
Default ACE-1
Default ACE-2
Default ACE-n
Deny any any
Mandatory rules from
parent policy
Default rules from
parent policy
Local rules in
child policy
Mandatory ACE-1
Mandatory ACE-2
Mandatory ACE-n
Local ACE-1
Local ACE-2
Local ACE-n
Default ACE-1
Default ACE-2
Default ACE-n
Deny any any
Mandatory ACE-1
Mandatory ACE-2
Mandatory ACE-n
Local ACE-1
Local ACE-2
Local ACE-n
Default ACE-1
Default ACE-2
Default ACE-n
Deny any any
Mandatory rules from
parent policy
Default rules from
parent policy
Local rules in
child policy
....
....
....
182194


















