6-27
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 6 Managing Policy Objects
Understanding AAA Server and Server Group Objects
When user authentication for VPN access has succeeded and the applicable tunnel-group policy
specifies an LDAP authorization server group, the ASA, PIX, or FWSM device queries the LDAP
server and applies the authorizations it receives to the VPN session.
• HTTP-Form—These devices can use the HTTP Form protocol for single sign-on (SSO)
authentication of WebVPN users only. Single sign-on support lets WebVPN users enter a username
and password only once to access multiple protected services and Web servers. The WebVPN server
running on the security appliance acts as a proxy for the user to the authenticating server. When a
user logs in, the WebVPN server sends an SSO authentication request, including username and
password, to the authenticating server using HTTPS. If the server approves the authentication
request, it returns an SSO authentication cookie to the WebVPN server. The security appliance keeps
this cookie on behalf of the user and uses it to authenticate the user to secure websites within the
domain protected by the SSO server.
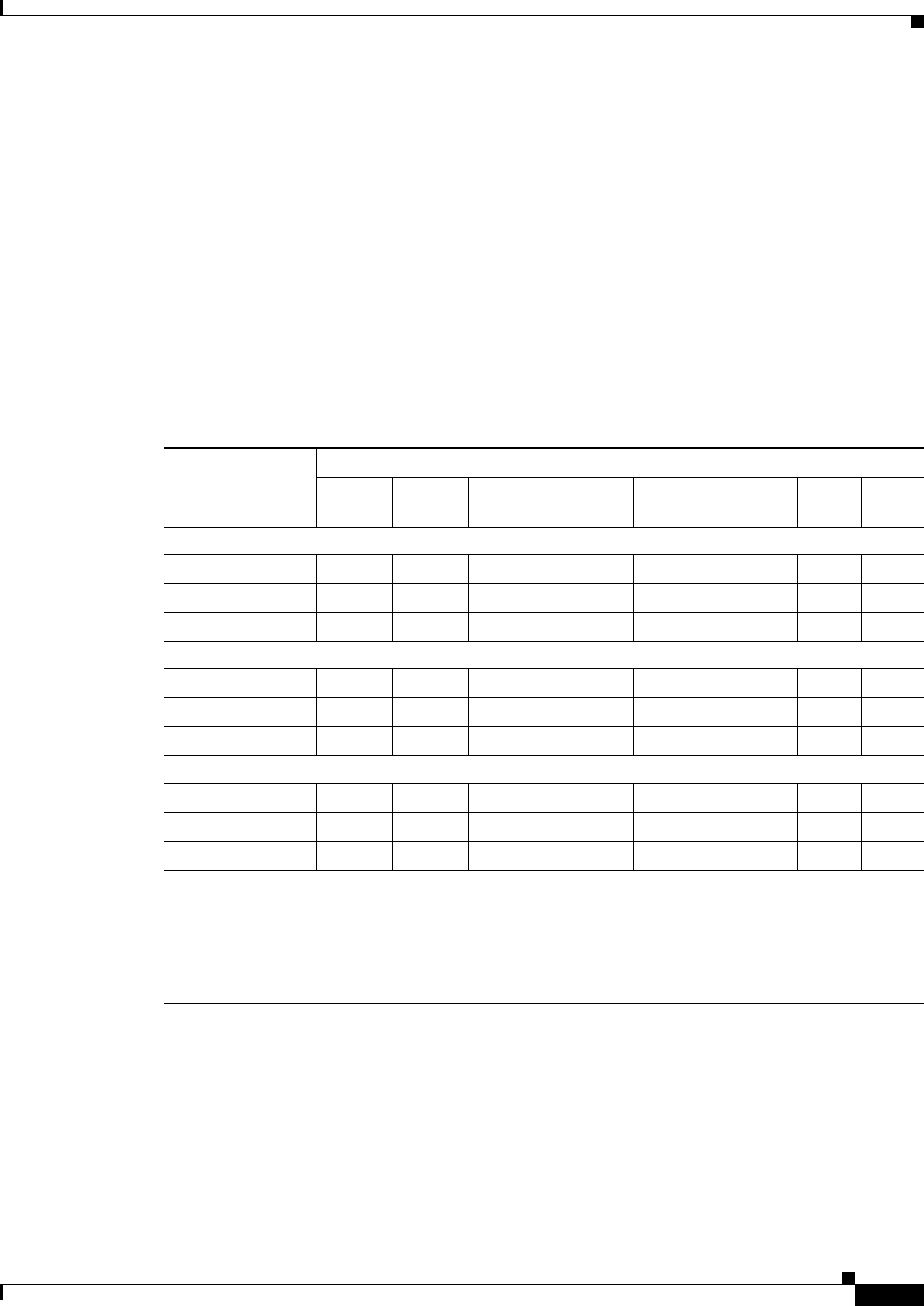
The following table describes the AAA services that are supported by each protocol:
Related Topics
• Supported AAA Server Types, page 6-25
• Creating AAA Server Objects, page 6-29
• Understanding AAA Server and Server Group Objects, page 6-24
Table 6-5 AAA Services Supported by ASA, PIX, and FWSM Devices
AAA Service
Database Type
Local RADIUS TACACS+ SDI NT Kerberos LDAP
HTTP
Form
Authentication of...
VPN users Yes Yes Yes Yes Yes Yes Yes Yes
1
Firewall sessions Yes Yes Yes Yes Yes Yes Yes No
Administrators Yes Yes Yes Yes
2
Yes Yes Yes No
Authorization of...
VPN users Yes Yes No No No No Yes No
Firewall sessions No Yes
3
Yes NoNoNo NoNo
Administrators Yes
4
NoYes NoNoNo NoNo
Accounting of...
VPN connections No Yes Yes No No No No No
Firewall sessionsNoYesYes NoNoNo NoNo
Administrators No Yes
5
Yes NoNoNo NoNo
1. HTTP Form protocol supports single sign-on (SSO) authentication for WebVPN users only.
2. SDI is not supported for HTTP administrative access.
3. For firewall sessions, RADIUS authorization is supported with user-specific ACLs only, which are received or specified in a RADIUS authentication
response.
4. Local command authorization is supported by privilege level only.
5. Command accounting is available for TACACS+ only.


















