16-37
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 16 Managing Firewall Access Rules
Importing Rules
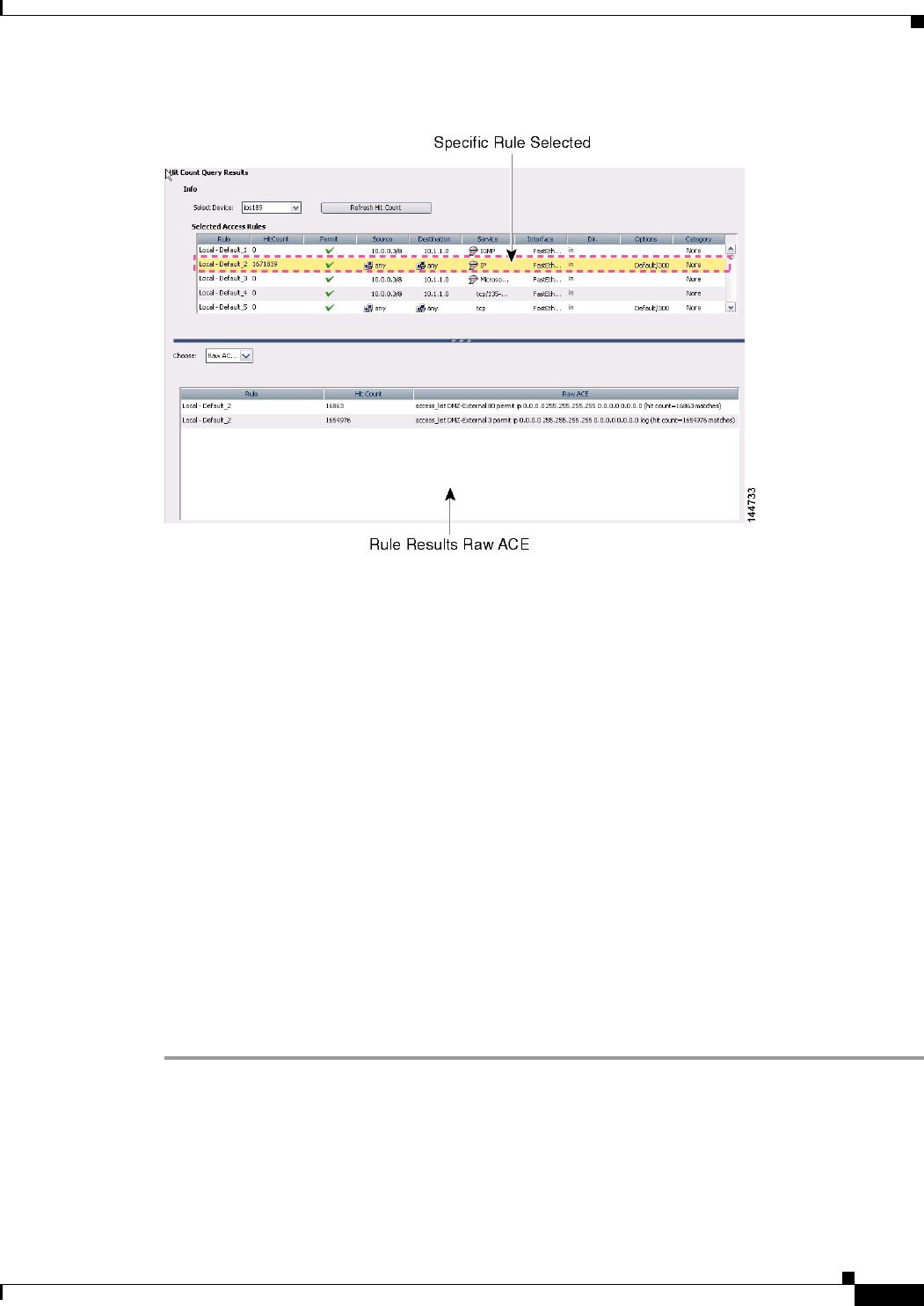
Figure 16-3 Raw ACE Table
Related Topics
• Understanding Access Rules, page 16-1
• Configuring Access Rules, page 16-7
Importing Rules
Typically, when you add a device to Security Manager, you discover policies from the device. This action
populates your access rules policy with the access control entries (ACEs) from all active ACLs on the
device.
If you find there are other ACLs that have ACEs you want included in your policy, you can define them
directly in Security Manager.
Another alternative, however, is to import them by copying and pasting the CLI entries from a device
running-configuration, or by typing in the desired commands. Using the Import Rules wizard, you can
quickly create ACEs and associated policy objects from ACLs that you know already work. You might
also want to use this method if you are more comfortable using CLI commands to define your rules.
The following steps describe using the Import Rules wizard to add CLI-based rules and preview the
results.
Step 1 (Device view only) Select Firewall > Access Rules to open the Access Rules Page, page 16-9.
Step 2 Select the row after which you want to add the rules. The row must be within the Local scope. If you do
not select a row, the rules are added at the end of the Local scope.
Step 3 Right-click anywhere in the rules table and choose Import Rules to start the wizard.
The first page—Enter Parameters—of the three-page wizard appears.


















