21-2
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 21 Managing Zone-based Firewall Rules
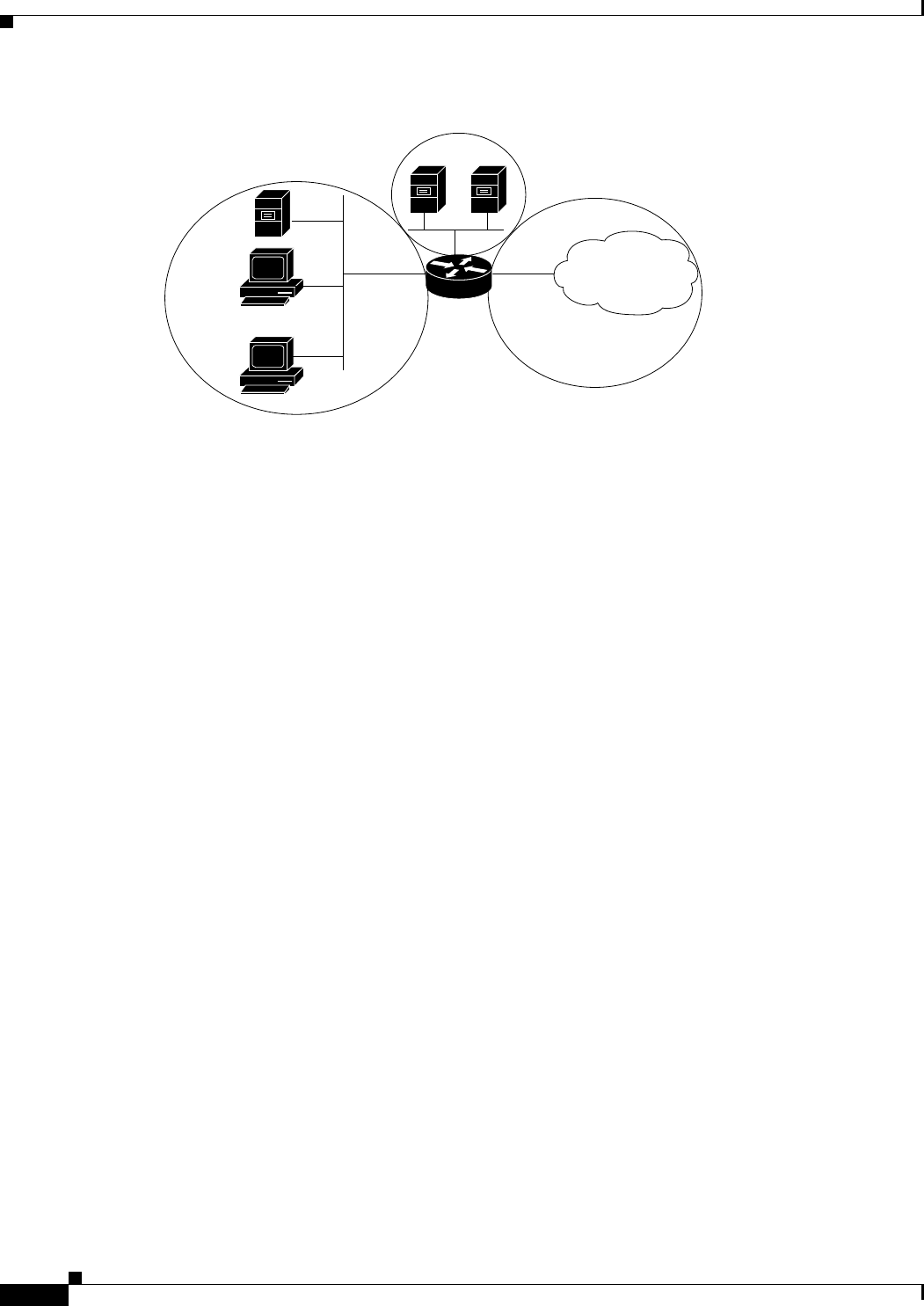
Figure 21-1 Basic Security Zone Topology
This example configuration typically would have three main policies (sets of rules) defining:
• Private zone connectivity to the Internet
• Private zone connectivity to DMZ hosts
• Internet zone connectivity to DMZ hosts
Zone-based firewalls impose a prohibitive default security posture. In other words, for example, unless
the DMZ hosts are specifically allowed access to other networks, those networks are protected against
any undesired connections from the DMZ hosts. Similarly, unless access is specifically provided for
Internet hosts to access the Private zone directly, the Private zone hosts are safe from unwanted access
by Internet hosts.
In this simple example, each zone has only one member interface. If an additional interface is added to
the Private zone, for example, the hosts connected to that new interface can immediately pass traffic to
all hosts connected to the existing interface in the zone. Additionally, traffic to hosts in other zones is
immediately controlled by existing Private zone policies.
In a more realistic example, you might allow varied access from the public Internet to specific hosts in
the DMZ, and varied application-use policies for hosts in the protected LAN.
This chapter contains the following topics:
• Understanding the Zone-based Firewall Rules, page 21-3
• Understanding the Relationship Between Permit/Deny and Action in Zone-based Firewall Rules,
page 21-7
• Understanding the Relationship Between Services and Protocols in Zone-based Firewall Rules,
page 21-10
• General Recommendations for Zone-based Firewall Rules, page 21-11
• Developing and Applying Zone-based Firewall Rules, page 21-12
• Adding Zone-Based Firewall Rules, page 21-12
• Configuring Inspection Maps for Zone-based Firewall Policies, page 21-15
• Configuring Content Filtering Maps for Zone-based Firewall Policies, page 21-35
• Changing the Default Drop Behavior, page 21-47
• Configuring Settings for Zone-based Firewall Rules, page 21-48
• Troubleshooting Zone-based Rules and Configurations, page 21-53
DMZ
Internet
Private
193017


















