21-6
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 21 Managing Zone-based Firewall Rules
Understanding the Zone-based Firewall Rules
interfaces in that security zone. Connections can be isolated in a VPN DMZ if connectivity must be
limited by a specific policy. Or, if VPN connectivity is implicitly trusted, VPN connections can be placed
in the same security zone as the trusted inside network.
To configure the router to use zone-based firewall rules with dynamic VPNs (those which dynamically
create Tunnel/Loopback/Virtual interfaces):
• Define a zone specifically for the VPN interfaces.
• Enter this zone in the VPN Zone field on the VPN tab of the Zone Based Firewall Page, page 21-49.
• Create zone-based firewall rules to allow the VPN traffic, as appropriate.
If non-VTI IPsec is employed, you must exercise caution when you configure a zone-based firewall
policy for VPN. The zone policy must specifically allow access to protected hosts by remote VPN hosts
or clients if they are in a different zone than the ingress interface for encrypted VPN traffic. This access
policy must be configured by including an access control list (ACL) enumerating the source IP addresses
of the VPN clients, and the destination IP addresses of all protected hosts the VPN clients are allowed
to reach. If the access policy is not properly configured, the policy could expose vulnerable hosts to
hostile traffic.
Refer to this white paper on cisco.com “Using VPN with Zone-Based Policy Firewall” for further
discussion of these topics.
Related Topics
• Understanding the Zone-based Firewall Rules, page 21-3
Zones and VRF-aware Firewalls
Cisco IOS firewalls are VRF-aware (Virtual Routing and Forwarding), providing management of IP
address overlap across different VRFs, separate thresholds and timeouts for VRFs, and so forth. For
application of zone-based firewall rules, all interfaces in a zone must belong to the same VRF.
When multiple VRFs are configured on a router and one interface provides common services to all the
VRFs (for example, Internet service), you should place that interface in a separate zone. You can then
define policies between the common zone and other zones. (There can be one or more zones per VRF.)
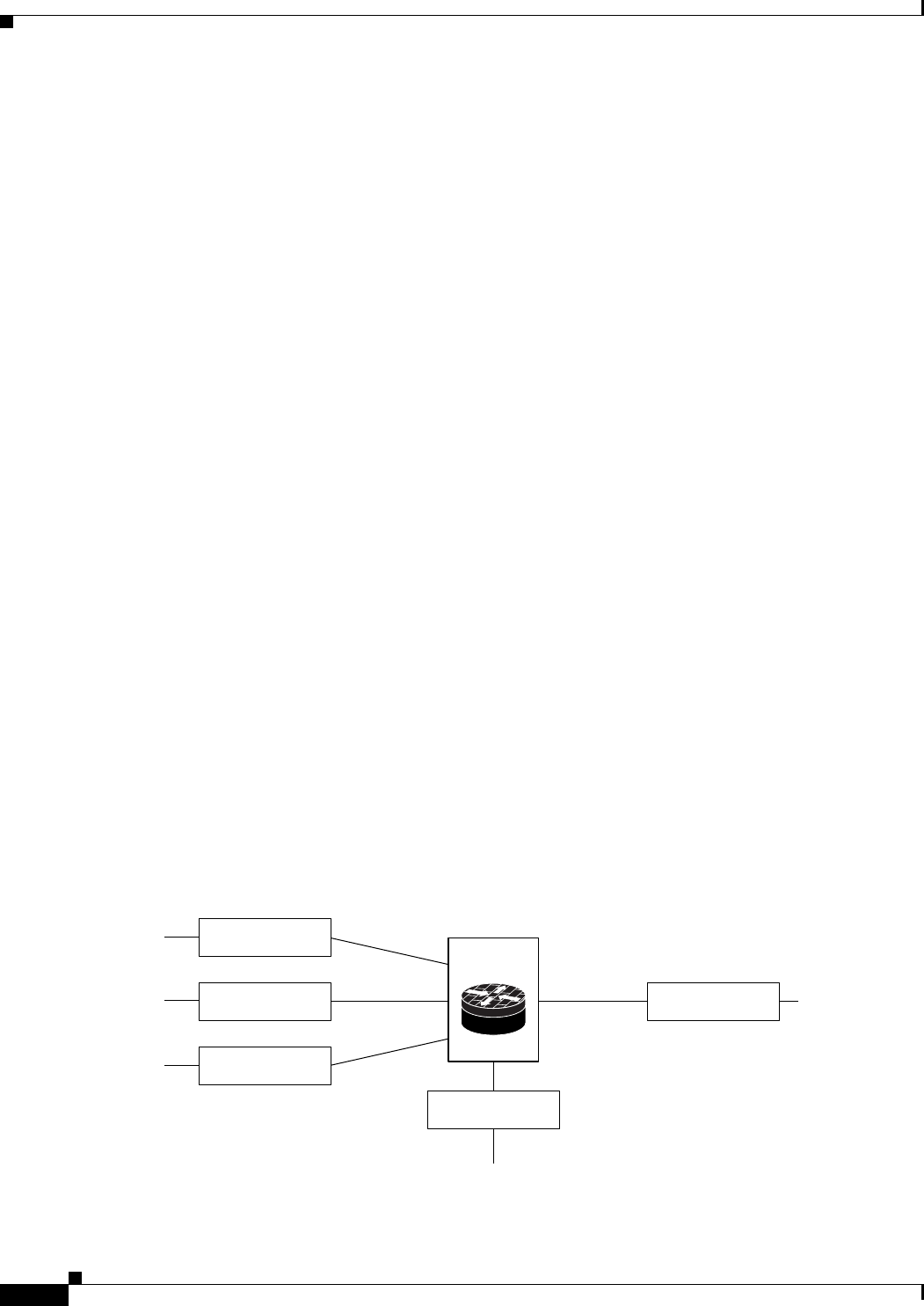
You can configure rules between two zones that contain different VRFs, as shown in the following
illustration.
Figure 21-2 Zones and VRF
Zone vrf_B_2
Zone Z1
Zone vrf_B_1 Zone common
Zone vrf_A
Firewall
Router
146618


















