24-3
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 24 Managing Site-to-Site VPNs: The Basics
Understanding VPN Topologies
A hub is generally located at an enterprise’s main office. Spoke devices are generally located at an
enterprise’s branch offices. In a hub-and-spoke topology, most traffic is initiated by hosts at the spoke
site, but some traffic might be initiated from the central site to the spokes.
If the hub in a hub-and-spoke configuration becomes unavailable for any reason, IPsec failover transfers
tunnel connections seamlessly to a failover (backup) hub, which is used by all spokes. You can configure
multiple failover hubs for a single primary hub.
In a hub-and-spoke VPN topology, all IPsec technology types can be assigned except GET VPN.
Related Topics
• Understanding IPsec Technologies and Policies, page 24-5
• Implicitly Supported Topologies, page 24-5
• Creating or Editing VPN Topologies, page 24-28
• Chapter 25, “Configuring IKE and IPsec Policies”
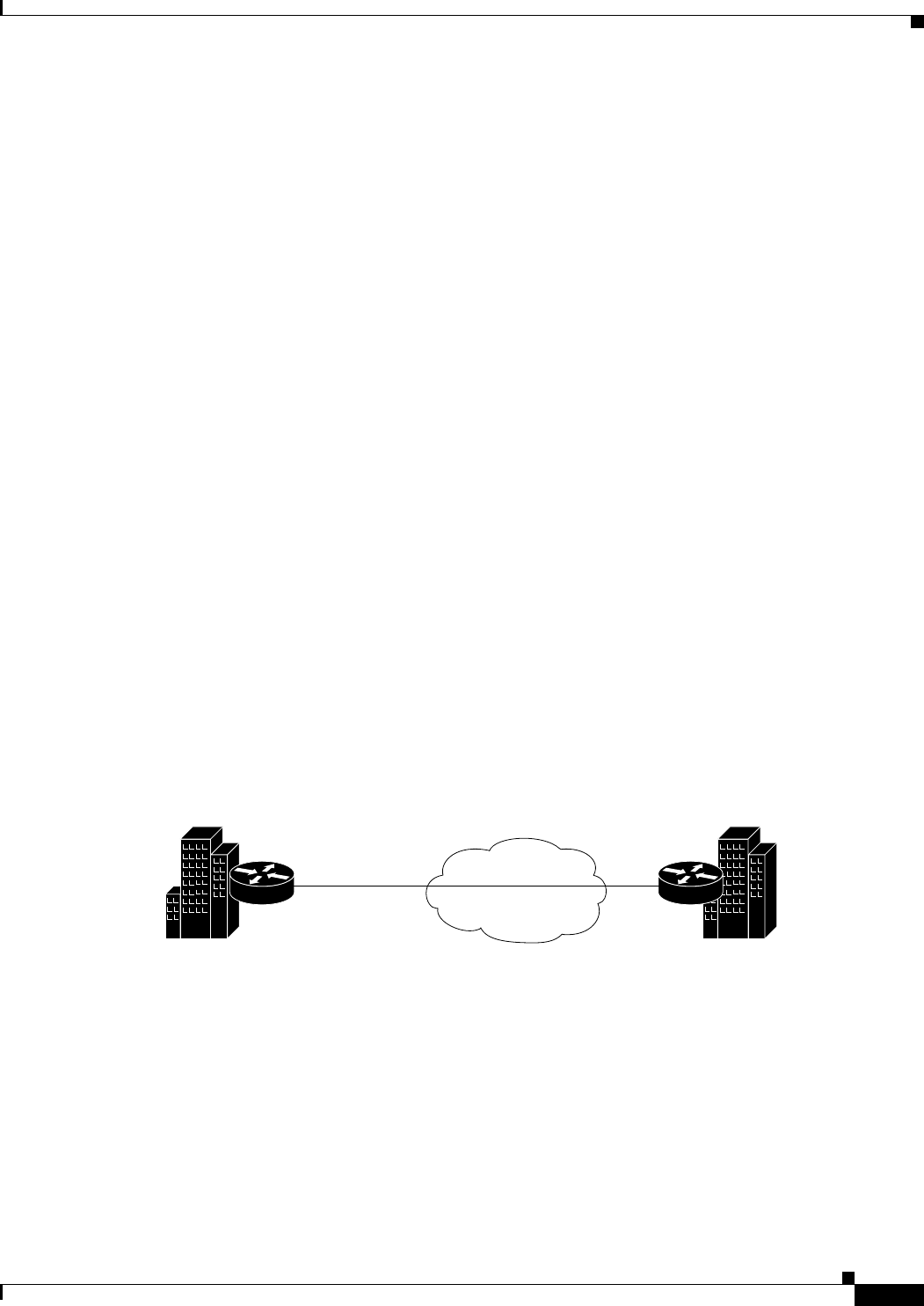
Point-to-Point VPN Topologies
In a point-to-point VPN topology, two devices communicate directly with each other, without the option
of IPsec failover as in a hub-and-spoke configuration. To establish a point-to-point VPN topology, you
specify two endpoints as peer devices. Because either of the two devices can initiate the connection, the
assigned IPsec technology type can be only regular IPsec or IPsec/GRE.
In Security Manager, you can configure a special type of regular IPsec point-to-point VPN called an
Extranet. An Extranet VPN is a connection between a device in your managed network and an
unmanaged device, such as a router in your service provider’s network, a non-Cisco device, or simply a
device in your network that is being managed by a different group (that is, one that does not appear in
the Security Manager inventory).
The following illustration shows a typical point-to-point VPN topology.
Figure 24-2 Point-to-Point VPN Topology
Related Topics
• Understanding IPsec Technologies and Policies, page 24-5
• Implicitly Supported Topologies, page 24-5
• Creating or Editing VPN Topologies, page 24-28
• Creating or Editing Extranet VPNs, page 24-63
• Chapter 25, “Configuring IKE and IPsec Policies”
Site 2Site 1
130053
Internet
Secure tunnel


















