3-2
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Chapter 3 ACS 5.x Policy Model
Overview of the ACS 5.x Policy Model
For example, we use the information described for the group-based model:
If identity-condition, restriction-condition then authorization-profile
In ACS 5.3, you define conditions and results as global, shared objects. You define them once and then
reference them when you create rules. ACS 5.3 uses the term policy elements for these shared objects,
and they are the building blocks for creating rules.
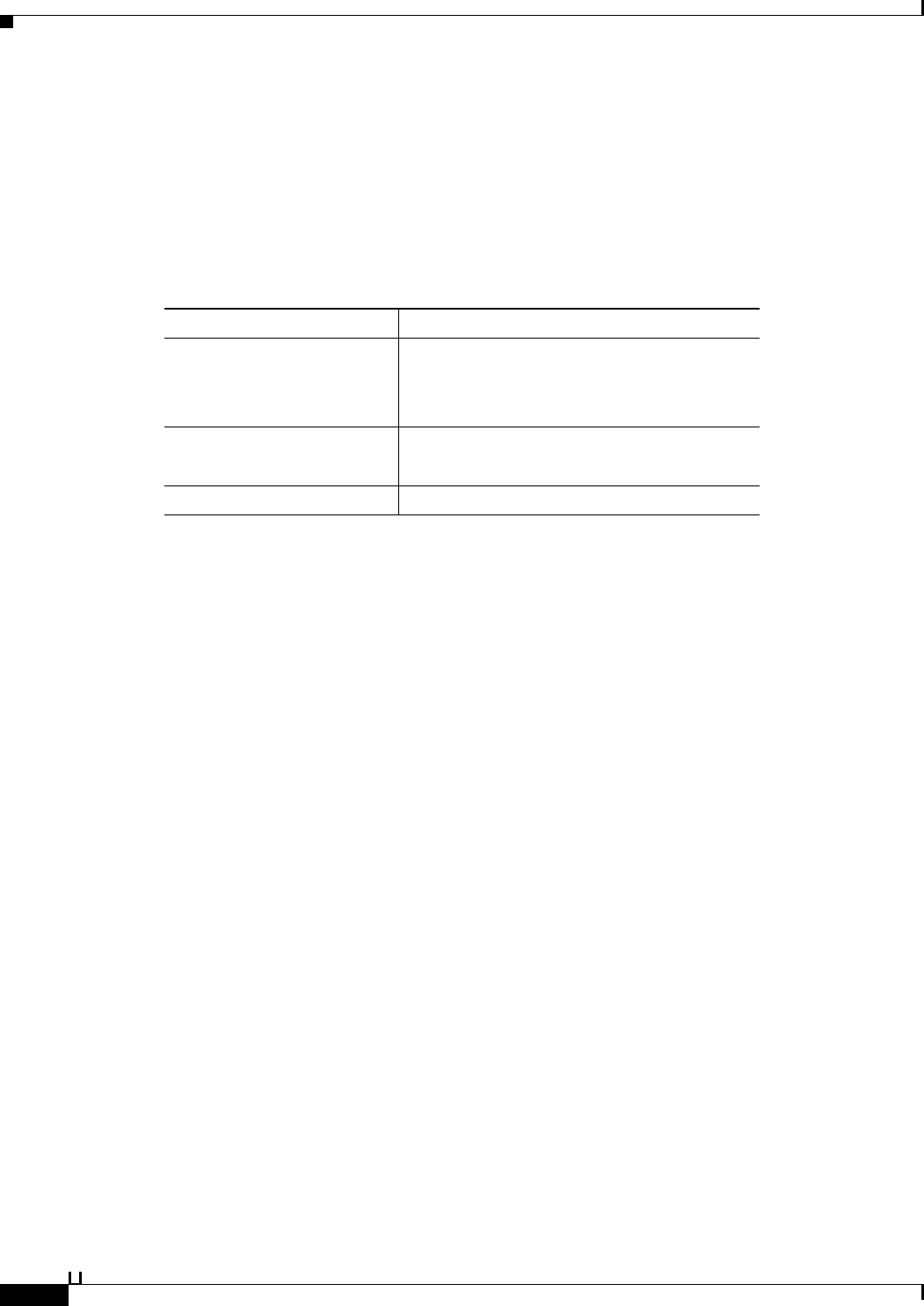
Table 3-1 shows how the various policy elements define all the information that the old group contained.
A policy is a set of rules that ACS 5.x uses to evaluate an access request and return a decision. For
example, the set of rules in an:
• Authorization policy return the authorization decision for a given access request.
• Identity policy decide how to authenticate and acquire identity attributes for a given access request.
ACS 5.x organizes the sequence of independent policies (a policy workflow) into an access service,
which it uses to process an access request. You can create multiple access services to process different
kinds of access requests; for example, for device administration or network access. For more
information, see Access Services, page 3-6.
You can define simple policies and rule-based policies. Rule-based policies are complex policies that
test various conditions. Simple policies apply a single result to all requests without any conditions.
There are various types of policies:
For more information on the different types of policies, see Types of Policies, page 3-5.
For more information about policy model terminology, see Policy Terminology, page 3-3.
Related Topics
• Policies and Identity Attributes, page 3-17
• Flows for Configuring Services and Policies, page 3-19
Table 3-1 Information in Policy Elements
Information in ACS 4.x Group Information in ACS 5.3 Policy Element
Identity information
• AD group membership and attributes
• LDAP group membership and attributes
• ACS internal identity groups and attributes
Other policy conditions
• Time and date conditions
• Custom conditions
Permissions Authorization profiles


















