A-3
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Appendix A AAA Protocols
Typical Use Cases
–
EAP protocols that involve a TLS handshake and in which the client uses the ACS server
certificate to perform server authentication:
PEAP, using one of the following inner methods: PEAP/EAP-MSCHAPv2 and
PEAP/EAP-GTC
EAP-FAST, using one of the following inner methods: EAP-FAST/EAP-MSCHAPv2 and
EAP-FAST/EAP-GTC
–
EAP protocols that are fully certificate-based, in which the TLS handshake uses certificates for
both server and client authentication:
EAP-TLS
For more information on RADIUS-based flows with EAP authentication, see RADIUS-Based Flows
with EAP Authentication, page A-3.
RADIUS-Based Flow Without EAP Authentication
This section describes RADIUS-based workflow without EAP authentication.
For RADIUS with PAP authentication:
1. A host connects to a network device.
2. The network device sends a RADIUS Access-Request to ACS, containing RADIUS attributes
appropriate to the specific protocol that is being used (PAP, CHAP, MSCHAPv1, or MSCHAPv2).
3. ACS uses an identity store to validate the user's credentials.
4. The RADIUS response (Access-Accept or Access-Reject) is sent to the network device that will
apply the decision.
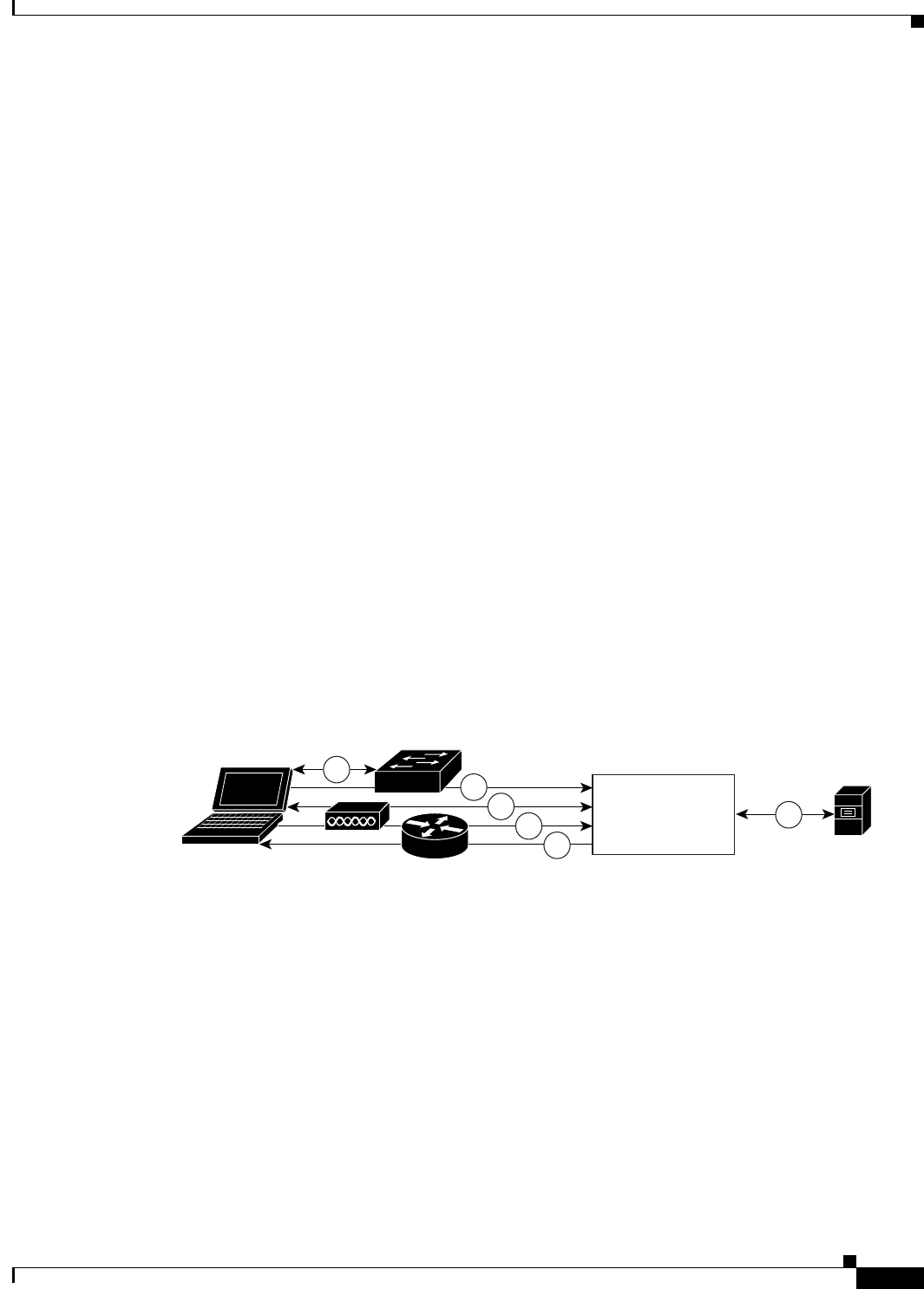
Figure A-2 shows a RADIUS-based authentication without EAP.
Figure A-2 RADIUS-Based Flow Without EAP Authentication
RADIUS-Based Flows with EAP Authentication
EAP provides an extensible framework that supports a variety of authentication types. Among them, the
specific EAP methods supported by ACS are:
• Simple EAP methods that do not use certificates:
–
EAP-MD5
–
LEAP
• EAP methods in which the client uses the ACS server certificate to perform server authentication:
–
PEAP/EAP-MSCHAPv2
–
PEAP/EAP-GTC
2
4
6
3
Host
Network device
ACS Runtime
5
Identity
store
250851
1


















