A-4
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Appendix A AAA Protocols
Typical Use Cases
–
EAP-FAST/EAP-MSCHAPv2
–
EAP-FAST/EAP-GTC
• EAP methods that use certificates for both server and client authentication
–
EAP-TLS
Whenever EAP is involved in the authentication process, it is preceded by an EAP negotiation phase to
determine which specific EAP method (and inner method, if applicable) should be used.
For all EAP authentications:
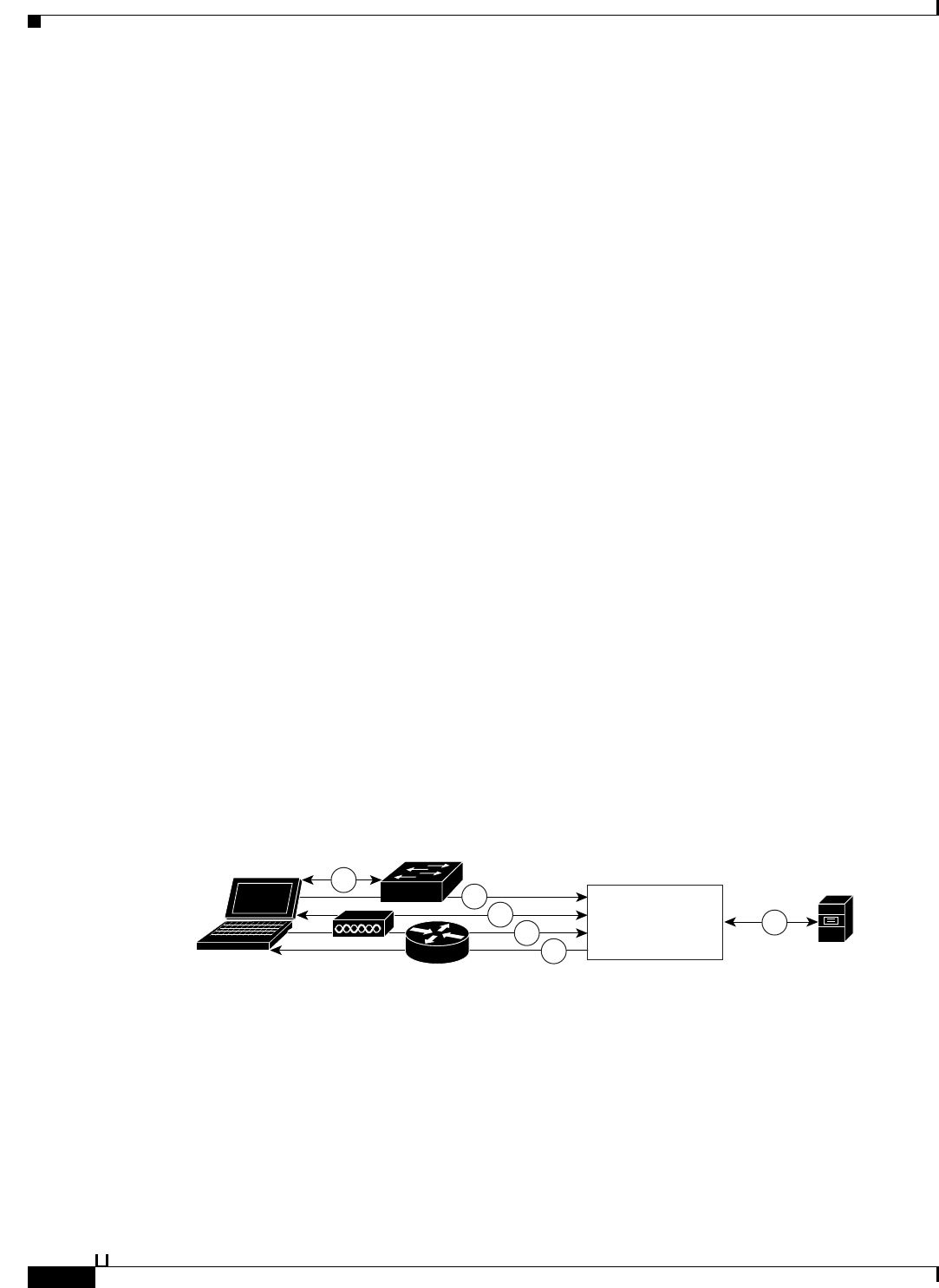
1. A host connects to a network device.
2. The network device sends an EAP Request to the host.
3. The host replies with an EAP Response to the network device.
4. The network device encapsulates the EAP Response that it received from the host into a RADIUS
Access-Request (using the EAP-Message RADIUS attribute) and sends the RADIUS
Access-Request to ACS.
5. ACS extracts the EAP Response from the RADIUS packet and creates a new EAP Request,
encapsulates it into a RADIUS Access-Challenge (again, using the EAP-Message RADIUS
attribute), and sends it to the network device.
6. The network device extracts the EAP Request and sends it to the host.
In this way, the host and ACS indirectly exchange EAP messages (transported over RADIUS and passed
through the network device). The initial set of EAP messages that are exchanged in this manner negotiate
the specific EAP method that will subsequently be used to perform the authentication.
The EAP messages that are subsequently exchanged are then used to carry the data needed to perform
the actual authentication. If required by the specific EAP authentication method that is negotiated, ACS
uses an identity store to validate the user's credentials.
After ACS determines whether the authentication should pass or fail, it sends either an EAP-Success or
EAP-Failure message, encapsulated into a RADIUS Access-Accept or Access-Reject message to the
network device (and ultimately also to the host).
Figure A-3 shows a RADIUS-based authentication with EAP.
Figure A-3 RADIUS-Based Authentication with EAP
For a list of known supplicant issues that might impact your ACS 5.3 experience, refer to
http://www.cisco.com/en/US/docs/net_mgmt/cisco_secure_access_control_system/5.3/release/notes/
acs_53_rn.html.
2
4
6
3
Host
Network device
ACS Runtime
5
Identity
store
250851
1


















