B-3
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Appendix B Authentication in ACS 5.3
EAP
RADIUS PAP Authentication
You can use different levels of security concurrently with ACS for different requirements. PAP applies
a two-way handshaking procedure. If authentication succeeds, ACS returns an acknowledgement;
otherwise, ACS terminates the connection or gives the originator another chance.
The originator is in total control of the frequency and timing of the attempts. Therefore, any server that
can use a stronger authentication method will offer to negotiate that method prior to PAP. RFC 1334
defines PAP.
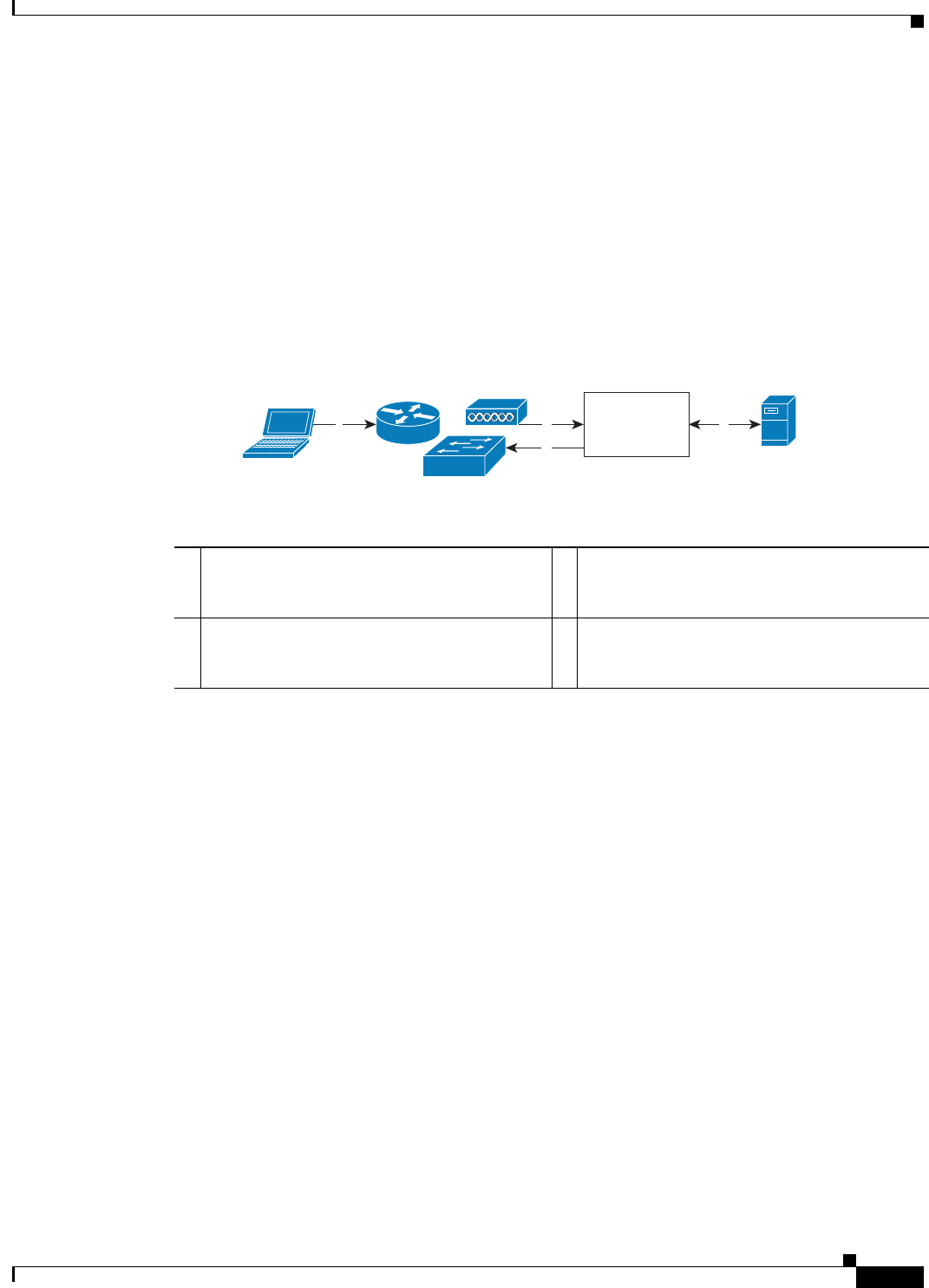
Figure B-1 illustrates RADIUS with PAP authentication.
Figure B-1 RADIUS with PAP Authentication Use Case
EAP
Extensible Authentication Protocol (EAP) is an authentication framework for wireless networks and
point-to-point connections. EAP supports multiple authentication methods, and provides common
functions and rules for negotiation of the desired authentication method:
• Server authentication request
• Client authentication response
• Server success authentication result
• Server failure authentication result
• Silent discard of client packets if they do not meet integrity and security conditions
• Rules for server-initiated EAP method negotiation
• Message sequencing, and tracking responses to requests
• Retransmit
EAP is a lock-step protocol; after the initial request, ACS cannot send a new request before receiving a
valid response from the client.
1 A host connects to the network. Any
communication protocol may be used
depending on the host.
3 ACS uses an external identity store to validate
the user's credentials.
2 The network device sends a RADIUS access
request to ACS.
4 The RADIUS response (Access-Accept or
Access-Reject) is sent to the network device
that will apply the decision.
Host
Network Device
2
4
1
External
Identity Store
3
210732
ACS Server


















