3-19
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Chapter 3 ACS 5.x Policy Model
Flows for Configuring Services and Policies
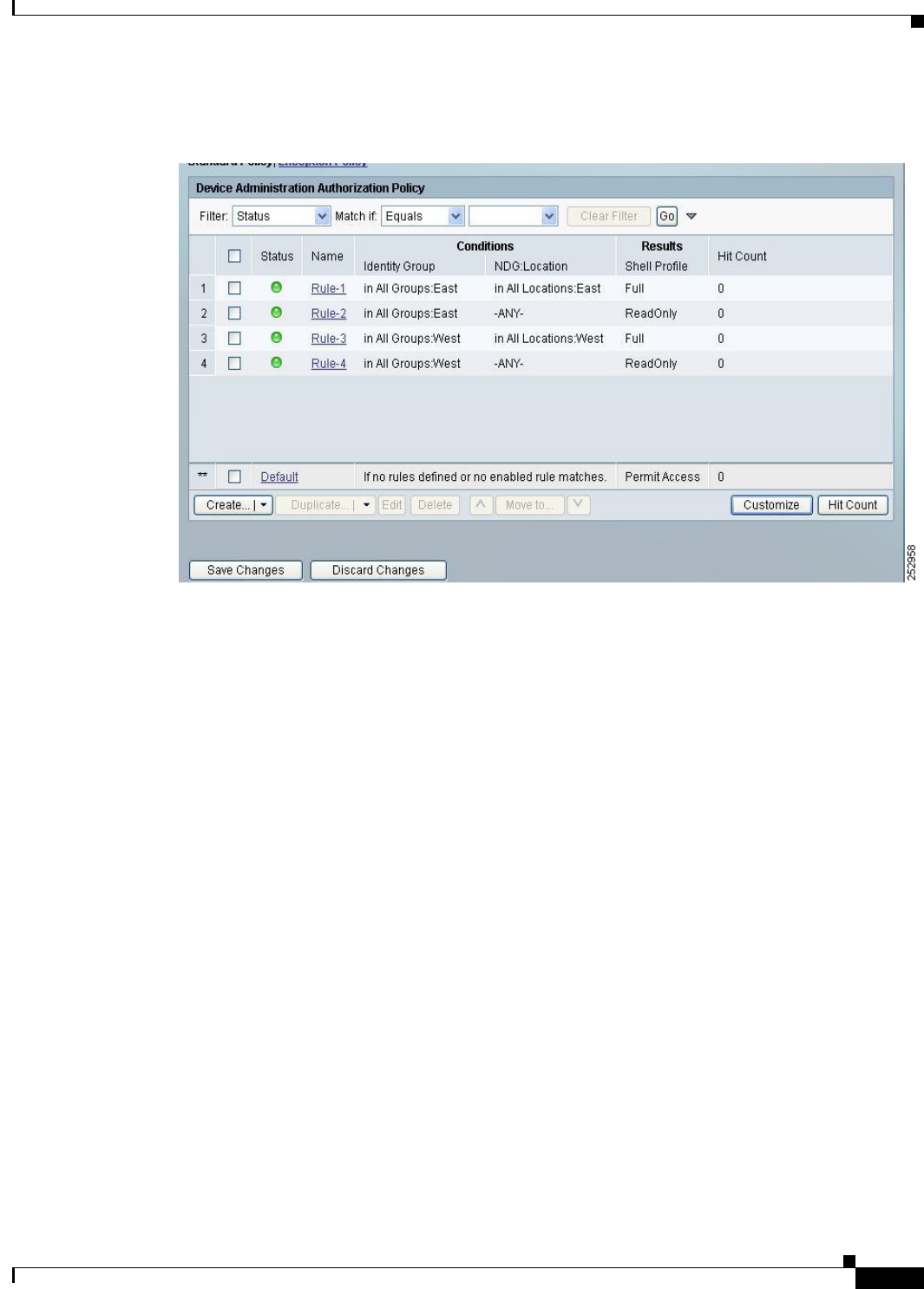
Figure 3-2 illustrates what this policy rule table could look like.
Figure 3-2 Sample Rule-Based Policy
Each row in the policy table represents a single rule.
Each rule, except for the last Default rule, contains two conditions, ID Group and Location, and a result,
Authorization Profile. ID Group is an identity-based classification and Location is a nonidentity
condition. The authorization profiles contain permissions for a session.
The ID Group, Location, and Authorization Profile are the policy elements.
Related Topics
• Policy Terminology, page 3-3
• Types of Policies, page 3-5
• Access Services, page 3-6
• Flows for Configuring Services and Policies, page 3-19
Flows for Configuring Services and Policies
Table 3-8 describes the recommended basic flow for configuring services and policies; this flow does
not include user-defined conditions and attribute configurations. With this flow, you can use NDGs,
identity groups, and compound conditions in rules.
Prerequisites
Before you configure services and policies, it is assumed you have done the following:
• Added network resources to ACS and create network device groups. See Creating, Duplicating, and
Editing Network Device Groups, page 7-2 and Network Devices and AAA Clients, page 7-5.


















