5-7
Cisco ONS 15600 Reference Manual, R7.2
Chapter 5 Security
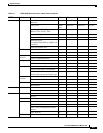
5.3.1 Audit Trail Log Entries
The audit trail is stored in persistent memory and is not corrupted by processor switches, resets or
upgrades. However, if a user pulls both TSC cards, the audit trail log is lost.
5.3.1 Audit Trail Log Entries
Audit trail records capture the following activities:
•
User—Name of the user performing the action
•
Host—Host from where the activity is logged
•
Device ID—IP address of the device involved in the activity
•
Application—Name of the application involved in the activity
•
Task—Name of the task involved in the activity (View a dialog, apply configuration and so on)
•
Connection Mode—Telnet, Console, SNMP
•
Category—Type of change; Hardware, Software, Configuration
•
Status—Status of the user action (Read, Initial, Successful, Timeout, Failed)
•
Time—Time of change
•
Message Type—Denotes if the event is Success/Failure type
•
Message Details—A description of the change
5.3.2 Audit Trail Capacities
The system is able to store 640 log entries.When this limit is reached, the oldest entries are overwritten
with new events. When the log server is 80 percent full, an AUD-LOG-LOW condition is raised and
logged (by way of CORBA/CTC).
When the log server reaches a maximum capacity of 640 entries and begins overwriting records that
were not archived, an AUD-LOG-LOSS condition is raised and logged. This event indicates that audit
trail records have been lost. Until the user off-loads the file, this event occurs once regardless of the
amount of entries that are overwritten by the system. To export the audit trail log, refer to the
Cisco ONS 15600 Procedure Guide.
5.4 RADIUS Security
Users with Superuser security privileges can configure nodes to use Remote Authentication Dial In User
Service (RADIUS) authentication. Cisco Systems uses a strategy known as authentication,
authorization, and accounting (AAA) for verifying the identity of, granting access to, and tracking the
actions of remote users.
5.4.1 RADIUS Authentication
RADIUS is a system of distributed security that secures remote access to networks and network services
against unauthorized access. RADIUS comprises three components:
•
A protocol with a frame format that utilizes User Datagram Protocol (UDP)/IP
•
A server