Intel
®
EP80579 Software for Security Applications on Intel
®
QuickAssist Technology
August 2009 PG
Order Number: 320183-004US 63
Using the Intel
®
QuickAssist Technology Cryptographic API—Security Software
4. The Cryptographic API makes a call to an internal function which handles the
operation and understands the message format to send to the SSU.
5. The Cryptographic API functions internally format the data as required by the
hardware and send it to the SSU.
6. The SSU performs the required crypto operation.
Note: At this point, behavior diverges depending on whether the function was
invoked synchronously or asynchronously.
7. The SSU after the operation is complete informs the software of the results via an
interrupt.
8. The Cryptographic API calls the opPerform completion callback, along with the
output data after formatting the data. This call executes in the context of a bottom
half.
1. The application or framework initializes a session using the API session initialization
function, this is a synchronous operation. During session initialization pre-
computes for Hash operations will be computed. This will involve a asynchronous
call to the Security Services Unit (SSU) which will return the pre-computes. This
only occurs during Hash operations. To the external Cryptographic API, this call is
synchronous as the asynchronous nature is handled internally in Cryptographic API.
The asynchronous part is hidden from the user by means of a queue.
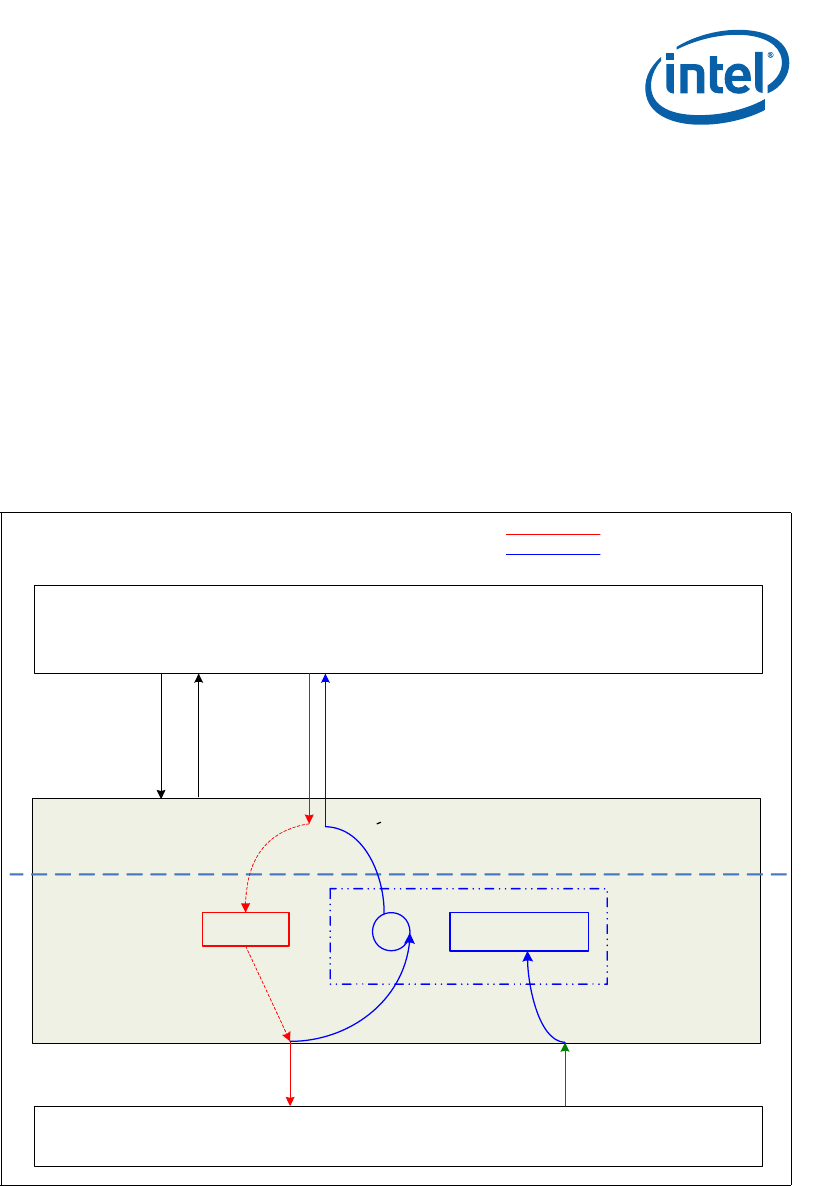
Figure 19. Symmetric Synchronous Intel
®
QuickAssist Technology Cryptographic API
Data Flow
Intel® QuickAssist Technology Cryptographic API
Security Access Library
Application or
Framework
Acceleration Services Unit (ASU)
(5)
(8)
(3) SymOpPerform
(IN a session ptr)
(1) Session Initialization
(IN func_ptr/NULL,
session_setup_data,
session ptr)
(2) Init Session
(OUT status)
(6)
wait
Sync
Internal callback
(7)
(9)
...
(4)
(10)
All modes
Synchronous modes


















