VIVOTEK - A Leading Provider of Multimedia Communication Solutions
42 - User's Manual
3�
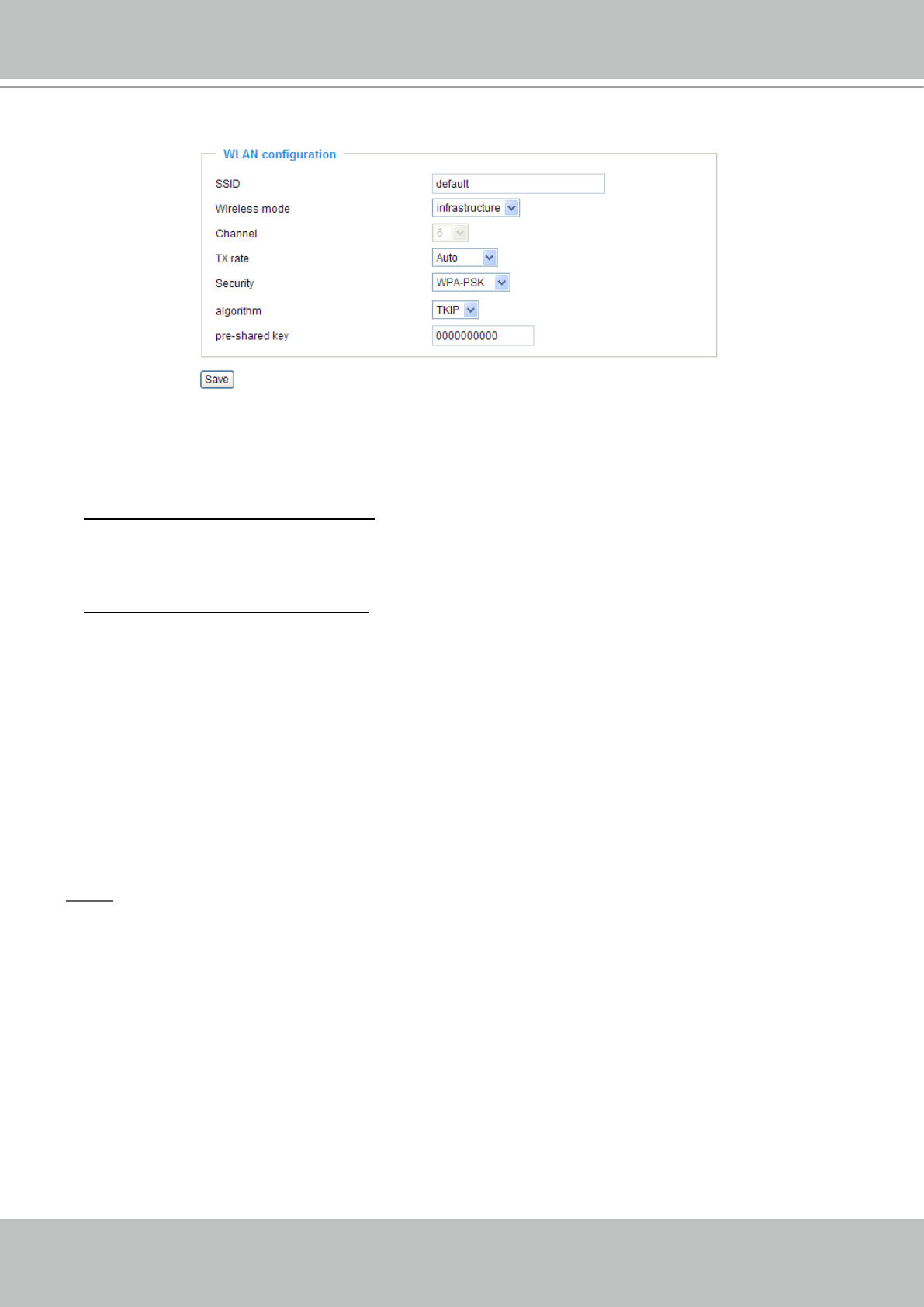
WPA-PSK: Use WPA (Wi-Fi Protected Access) pre-shared key�
More secure than WEP, the Wi-Fi Alliance developed WPA (Wi-Fi Protected Access) in 2003 to
address WEP’s weaknesses� Improvements included TKIP, which changes the encryption key for each
data transmission�
■
Algorithm: Choosing one of the following algorithm for WPA-PSK and WPA2-PSK modes�
TKIP (Temporal Key Integrity Protocol): A security protocol used in the IEEE 802�11 wireless networks�
TKIP is a “wrapper” that goes around the existing WEP encryption� TKIP comprises the same
encryption engine and RC4 algorithm dened for WEP. However, the key used for encryption in TKIP
is 128 bits long. This solves the rst problem of WEP: a too-short key length. (From Wikipedia)
AES (Advanced Encryption Standard): In cryptography, the Advanced Encryption Standard (AES),
also known as Rijndael, is a block cipher adopted as an encryption standard by the U�S� government�
As of 2006, AES is one of the most popular algorithms used in symmetric key cryptography� (From
Wikipedia)
■
Pre-shared Key: Entering a key in ASCII format� The length of the key is 8 ~ 63�
4�
WPA2-PSK: Use WPA2 pre-shared key�
The advanced protocol, certied through Wi-Fi Alliance’s WPA2 program, implements the mandatory
elements of 802�11i� In particular, it introduces a new AES-based algorithm, CCMP, that is considered
fully secure. From March 13, 2006, WPA2 certication is mandatory for all new devices wishing to be
certied by the Wi-Fi Alliance as “Wi-Fi CERTIFIED.” (From Wikipedia)
NOTE
► After wireless congurations are completed, click Save and the camera will reboot� Wait for the live
image is reloaded to your browser� For VIVOTEK 7000-series cameras, you have to unplug the power
cable and Ethernet cable from the camera; then re-plug the power cable to the camera� The camera
will switch to wireless mode�
► Some invalid settings may cause the system failing to respond. Change the Conguration only if
necessary and consult with your network supervisor or experienced users for correct settings� Once
the system has lost contact, please refer to Maintenace on page 75 for reset and restore procedures�