44
AXIS 233D - System Options
Clients and servers in an 802.1X network may need to authenticate each other by some
means. In the Axis implementation this is done with the help of digital certificates
provided by a Certification Authority (CA). These are then validated by a third-party
entity, such as a RADIUS server, examples of which are Free Radius and Microsoft Internet
Authentication Service.
To perform the authentication, the RADIUS server uses various EAP methods/protocols, of
which there are many. The one used in the Axis implementation is EAP-TLS
(EAP-Transport Layer Security).
The AXIS network video device presents its certificate to the network switch, which in turn
forwards this to the RADIUS server. The RADIUS server validates or rejects the certificate
and responds to the switch, and sends its own certificate to the client for validation. The
switch then allows or denies network access accordingly, on a pre-configured port.
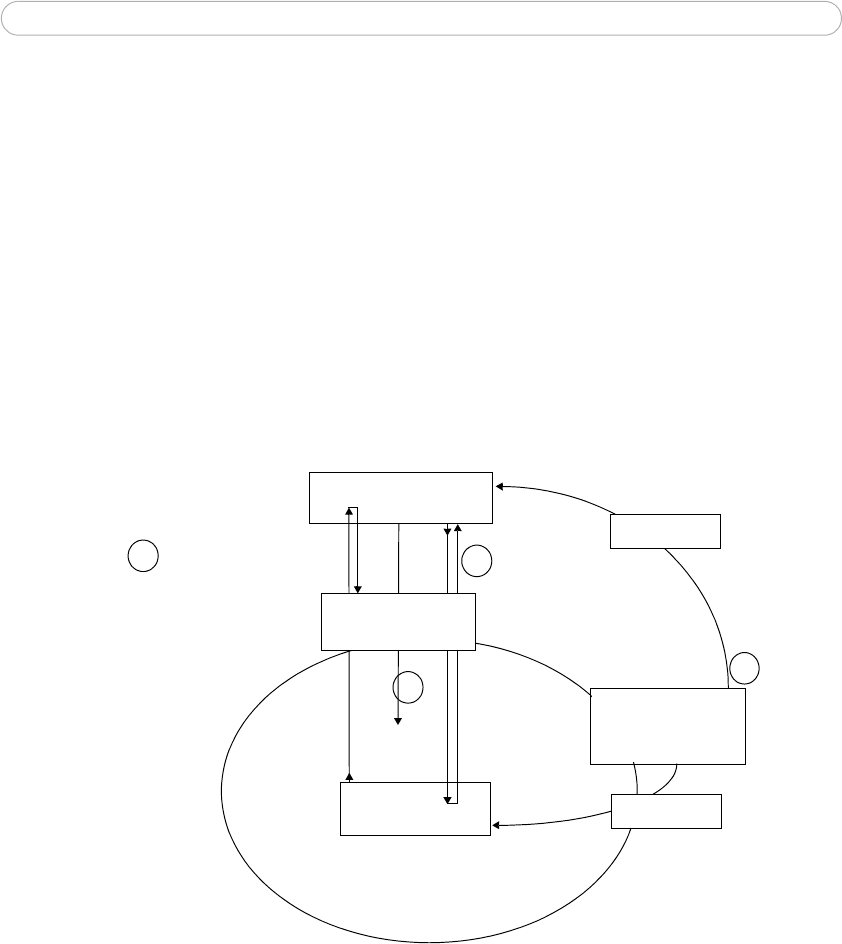
The authentication process
1. A CA server provides the required signed certificates.
2. The Axis video device requests access to the protected network at the network
switch. The switch forwards the video device’s CA certificate to the RADIUS server,
which then replies to the switch.
3. The switch forwards the RADIUS server’s CA certificate to the video device, which
also replies to the switch.
Protected network
Axis video device
Q: Certificate OK?
Certificate
Authority (CA)
3
1
2
4
A: OK
RADIUS
server
Network
switch
Q: Certificate OK?
A: OK
Certificate
Certificate


















