Network Data Encryption
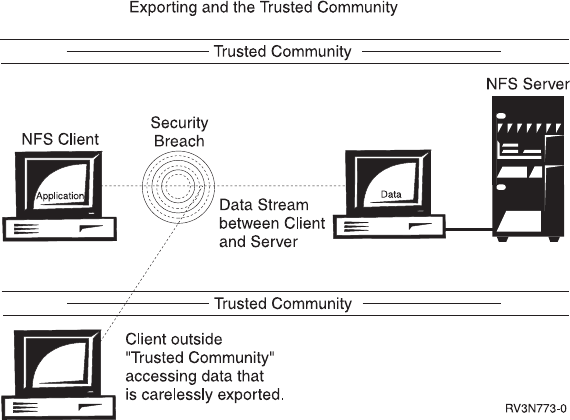
A client existing outside the trusted community can become aware of the
community’s existence. Furthermore, a malignant client can introduce a “sniff”
program that can read and change data as it transfers in the client/server
relationship. It accomplishes this by intercepting the data flow and altering the data
on contact. The system sends unencrypted data as plain text between the client
and server. Therefore, any system that is “sniffing” for such data can access it for
reading by interacting with the token ring, ethernet, or other network interfaces.
There are various ways to protect the individual servers and clients in the
community from outside intruders. There are also methods of protecting data as it is
being sent from client to server and back again:
1. Users can code data with encryption engines, if they are located on both the
client and the server. These engines code information as it leaves the “source”
client or server and then decode the information when it reaches the “target”
client or server.
2. The identities of users can be authenticated using the following methods:
a. AUTH_UNIX. Authorization to objects is controlled by user identification
(UID) only. There is no encryption whatsoever. AS/400 automatically
performs this type of object authorization.
b. AUTH_DES. This is the Data Encryption Standard (DES). Using this type of
encryption will protect data.
c. AUTH_KERBEROS. This type of encryption protects the user through a third
party administrator who administers authority tokens that are based on a
trusted token manager. Kerberos security can enforce the trusted
community. Kerberos is the authentication protocol used to implement
private key authorization. Kerberos relies on complete and total
authentication of users and authorities within the trusted community, allowing
no one else access to data.
Figure 58. Client outside the trusted community causing a security breaches
82 OS/400 Network File System Support V4R4
|
|
|
|
|
|
|


















