Chapter 21 Anti-Virus
ZyWALL (ZLD) CLI Reference Guide
176
21.2.2.1 Zone to Zone Anti-virus Rule Example
This example shows how to configure (and display) a WAN to LAN antivirus rule to scan HTTP traffic
and destroy infected files. The white and black lists are ignored and zipped files are decompressed.
Any zipped files that cannot be decompressed are destroyed.
21.2.3 White and Black Lists
The following table describes the commands for configuring the white list and black list. You must
use the
configure terminal command to enter the configuration mode before you can use
these commands.
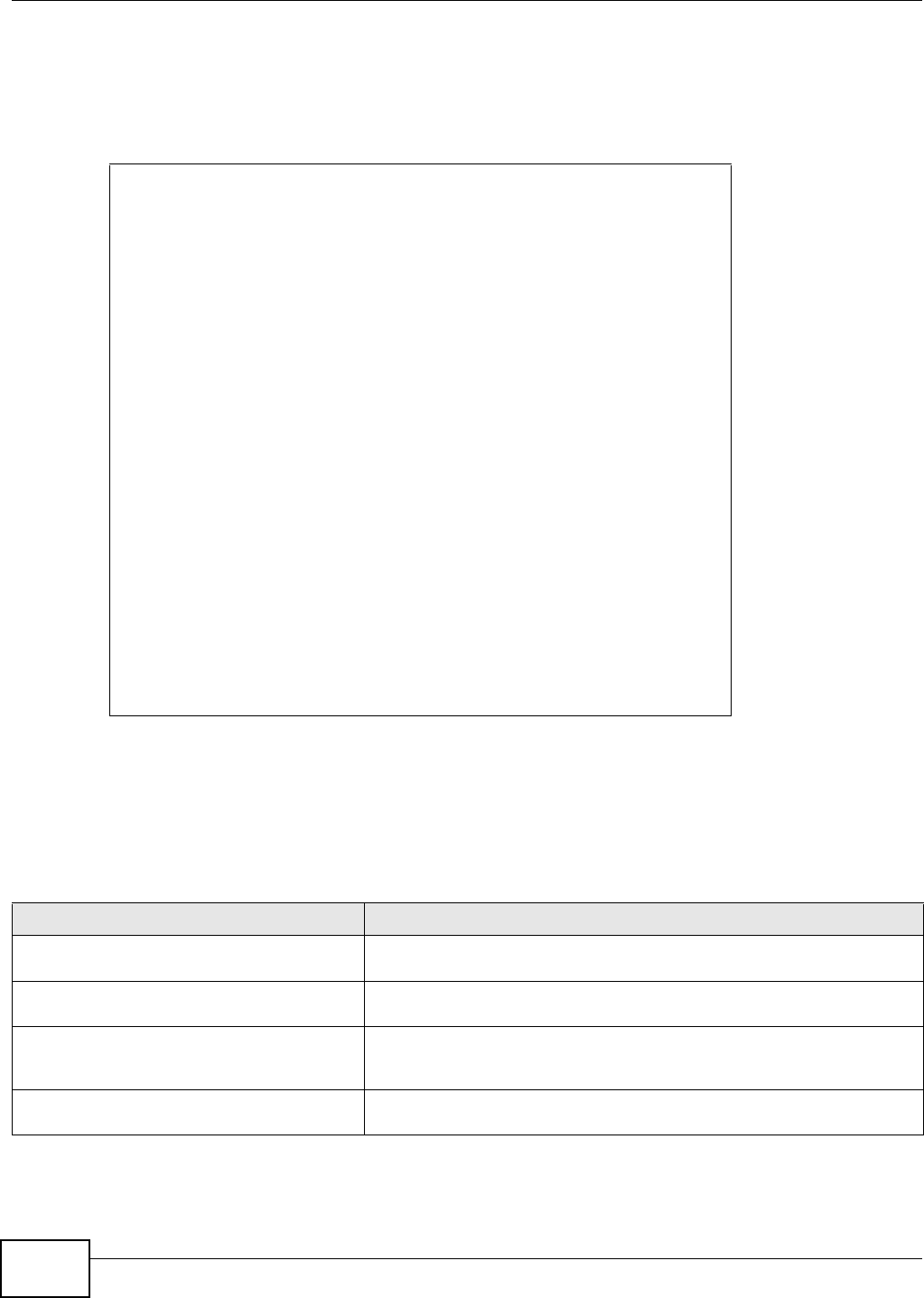
Router(config)# anti-virus rule 1
Router(config-av-rule-1)# activate
Router(config-av-rule-1)# from-zone WAN
Router(config-av-rule-1)# to-zone LAN
Router(config-av-rule-1)# scan http
Router(config-av-rule-1)# infected-action destroy
Router(config-av-rule-1)# bypass white-list
Router(config-av-rule-1)# no bypass black-list
Router(config-av-rule-1)# file-decompression
Router(config-av-rule-1)# no file-decompression unsupported destroy
Router(config-av-rule-1)# exit
Router(config)# show anti-virus rule 1
Anti-Virus Rule: 1
active: yes
log: log
from zone: WAN
to zone: LAN
scan protocols:
http: yes
ftp : yes
smtp: yes
pop3: yes
imap4: yes
infected action:
destroy: yes
send windows message: yes
bypass white list: yes
bypass black list: no
file decompression: yes
destroy unsupported compressed file: no
Table 94 Commands for Anti-virus White and Black Lists
COMMAND DESCRIPTION
[no] anti-virus white-list activate Turn on the white list to have the ZyWALL not perform the anti-virus check
on files with names that match the white list patterns.
[no] anti-virus white-list file-pattern
av_file_pattern {activate|deactivate}
Adds or removes a white list file pattern. Turns a file pattern on or off.
anti-virus white-list replace
old_av_file_pattern new_av_file_pattern
{activate|deactivate}
Replaces the specified white list file pattern with a new file pattern.
[no] anti-virus black-list activate Turn on the black list to log and delete files with names that match the
black list patterns.


















