11-3
Cisco IOS Software Configuration Guide for Cisco Aironet Access Points
OL-30644-01
Chapter 11 Configuring Authentication Types
Understanding Authentication Types
In a scenario where you use Open authentication and WEP encryption, authentication will be successful
even if the client and the AP WEP are mismatched. The client will not be able to send data (including
DHCP requests) after Open authentication completes. However, with Open authentication and no
encryption, the wireless client can transmit data as soon as the association phase is complete.
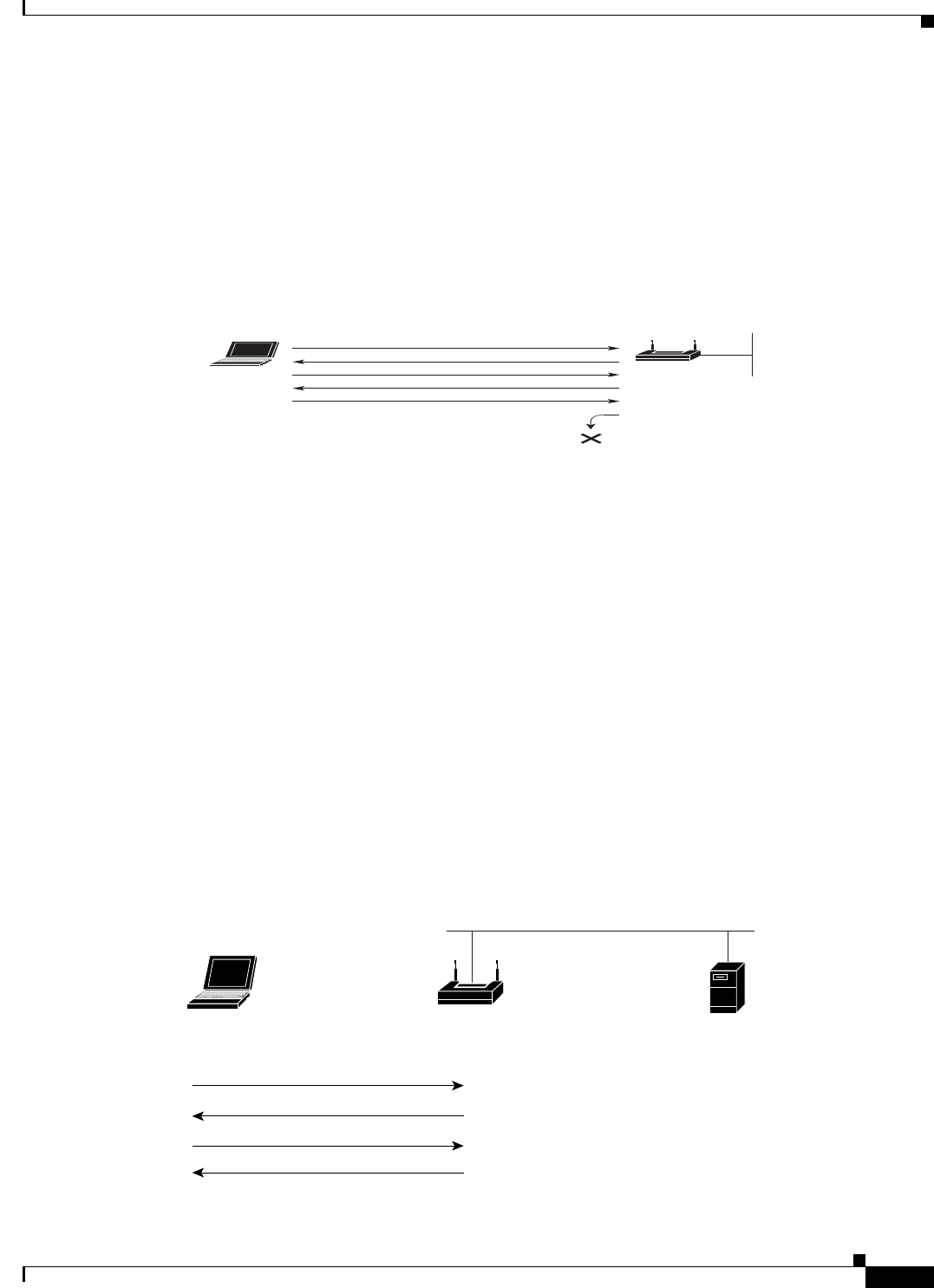
Figure 11-1 shows the authentication sequence between a device trying to authenticate and an access
point using open authentication. In this example, the device’s WEP key does not match the access point’s
key, so it can authenticate but not pass data.
Figure 11-1 Sequence for Open Authentication
WEP Shared Key Authentication to the Access Point
Cisco provides shared key authentication to comply with WEP authentication described in the 802.11
standard. However, because of a shared key’s security flaws WEP has been deprecated. The IEEE and
Cisco recommend that you avoid using it.
During shared key authentication, the access point sends an unencrypted challenge text string to any
device attempting to communicate with the access point. The device requesting authentication encrypts
the challenge text and sends it back to the access point. If the challenge text is encrypted correctly, the
access point allows the requesting device to authenticate. Both the unencrypted challenge and the
encrypted challenge can be monitored, however, which leaves the access point open to attack from an
intruder who calculates the WEP key by comparing the unencrypted and encrypted text strings. Because
of this weakness, shared key authentication can be less secure than open authentication. Like open
authentication, shared key authentication does not rely on a RADIUS server on your network.
Figure 11-2 shows the authentication sequence between a device trying to authenticate and an access
point using shared key authentication. In this example the device’s WEP key matches the access point’s
key, so it can authenticate and communicate.
Figure 11-2 Sequence for Shared Key Authentication
Access point
or bridge
with WEP key = 123
Client device
with WEP key = 321
1. Authentication request
2. Authentication response
4. Association response
6. Key mismatch, frame discarded
3. Association request
5. WEP data frame to wired network
54583
Access point
or bridge
Wired LAN
Client
device
Server
1. Authentication request
2. Unencrypted challenge text
3. Encrypted challenge text
4. Authentication success
231083


















