12-3
Cisco IOS Software Configuration Guide for Cisco Aironet Access Points
OL-30644-01
Chapter 12 Configuring WDS, Fast Secure Roaming, Radio Management, and Wireless Intrusion Detection Services
Understanding Fast Secure Roaming
Role of Access Points Using the WDS Device
The access points on your wireless LAN interact with the WDS device in these activities:
• Discover and track the current WDS device and relay WDS advertisements to the wireless LAN.
• Authenticate with the WDS device and establish a secure communication channel to the WDS
device.
• Register associated client devices with the WDS device.
• Report radio data to the WDS device.
Understanding Fast Secure Roaming
Access points in many wireless LANs serve mobile client devices that roam from access point to access
point throughout the installation. Some applications running on client devices require fast reassociation
when they roam to a different access point. Voice applications, for example, require seamless roaming
to prevent delays and gaps in conversation.
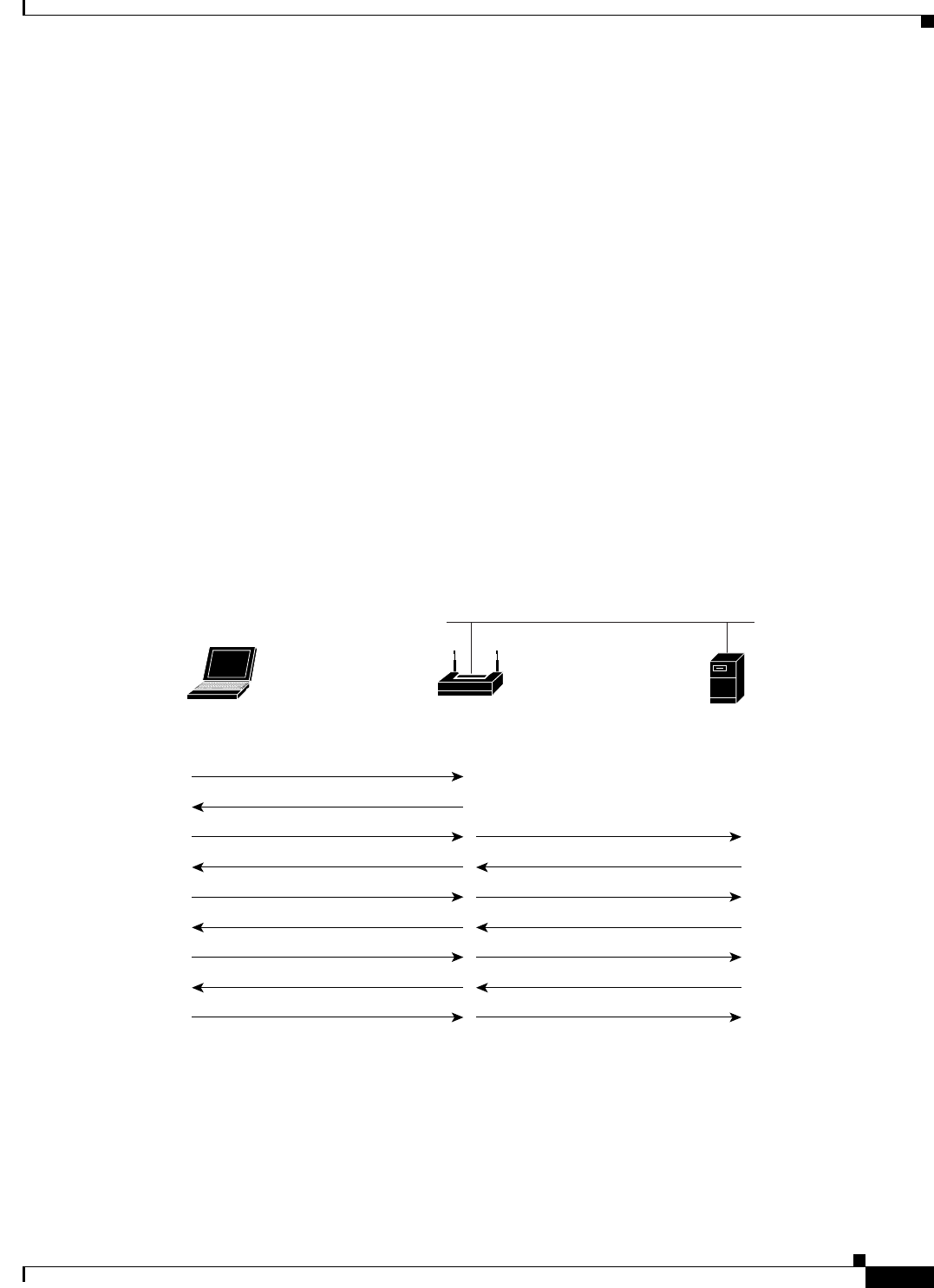
During normal operation, EAP/802.1x-enabled client devices mutually authenticate with a new access
point by performing a complete EAP/802.1x authentication, including communication with the main
RADIUS server, as in Figure 12-1.
Figure 12-1 Example of Client Authentication Exchange using a RADIUS Server (LEAP case)
When you configure your wireless LAN for fast, secure roaming, however, EAP/802.1x-enabled client
devices roam from one access point to another without involving the main RADIUS server. Using Cisco
Centralized Key Management (CCKM), a device configured to provide Wireless Domain Services
(WDS) takes the place of the RADIUS server and authenticates the client so quickly that there is no
perceptible delay in voice or other time-sensitive applications. Figure 12-2 shows client authentication
using CCKM.
Access point
or bridge
Wired LAN
Client
device
RADIUS Server
1. Authentication request
2. Identity request
3. Username
(relay to client)
(relay to server)
4. Authentication challenge
5. Authentication response
(relay to client)
(relay to server)
6. Authentication success
7. Authentication challenge
(relay to client)
(relay to server)
8. Authentication response
9. Successful authentication
(relay to server)
65583


















