RealPresence Collaboration Server (RMX) 1500/1800/2000/4000 Administrator’s Guide
Polycom®, Inc. 459
Regular users can connect from any workstation having a valid certificate while application-users
representing applications can only connect from specific servers. This policy ensures that a regular user
cannot impersonate an application-user to gain access to the Collaboration Server in order to initiate an
attack that would result in a Denial of Service (DoS) to the impersonated application.
The connection process for an application-user connecting to the Collaboration Server is as follows:
1 The application-user sends a connection request, including its TLS certificate, to the Collaboration
Server.
2 The Collaboration Server searches its records to find the FQDN that is associated with the
application-user’s name.
3 If the FQDN in the received certificate matches that associated with application-user, and the
password is correct, the connection proceeds.
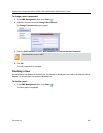
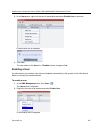
Guidelines for defining a machine account
● Application-users are only supported when TLS security is enabled and Request peer certificate is
selected. TLS security cannot be disabled until all application-user accounts have been deleted from
the system.
● For Secure Communications, an administrator must set up on the Collaboration Server system a
machine account for the RealPresence CMA/DMA/XMA system with which it interacts. This machine
account must include a fully-qualified domain name (FQDN) for the RealPresence CMA/DMA/XMA
system.
● Application-user names are the same as regular user names.
Example: the CMA application could have an application-user name of CMA1.
● The FQDN can be used to associate all user types: Administrator, Operator with the FQDN of a
server.
● Multiple application-users can be configured the same FQDN name if multiple applications are
hosted on the same server
● If the system is downgraded the application-user’s FQDN information is not deleted from the
Collaboration Server’s user records.
● A System Flag, PASS_EXP_DAYS_MACHINE, enables the administrator to change the password
expiration period of application-user’s independently of regular users. The default flag value is 365
days.
● The server hosting an application-user whose password is about to expire will receive a login
response stating the number of days until the application-user’s password expires. This is determined
by the value of the PASSWORD_EXPIRATION_WARNING_DAYS System Flag. The earliest
warning can be displayed 14 days before the password is due to expire and the latest warning can
be displayed 7 days before passwords are due to expire. An Active Alarm is created stating the
number of days before the password is due to expire.
● The MIN_PWD_CHANGE_FREQUENCY_IN_DAYS System Flag does not effect application-user
accounts. Applications typically manage their own password change frequency.
● If an application-user identifies itself with an incorrect FQDN, its account will not be locked, however
the event is written to the Auditor Event File.
● If an application-user identifies itself with a correct FQDN and an incorrect password, its account will
be locked and the event written to the Auditor Event File.
● An application-user cannot be the last administrator in the system. The last administrator must be
regular user.