12-17
User Guide for Cisco Secure Access Control System 5.3
OL-24201-01
Chapter 12 Managing Alarms
Creating, Editing, and Duplicating Alarm Thresholds
An alarm is triggered because at least one Device IP has greater than 10 failed authentications in the past
2 hours.
Note You can specify one or more filters to limit the failed authentications that are considered for threshold
evaluation. Each filter is associated with a particular attribute in the authentication records and only
those records whose filter value matches the value that you specify are counted. If you specify multiple
filters, only the records that match all the filter conditions are counted.
Modify the fields in the Criteria tab as described in Table 12-11 to create a threshold with the failed
authentication criteria.
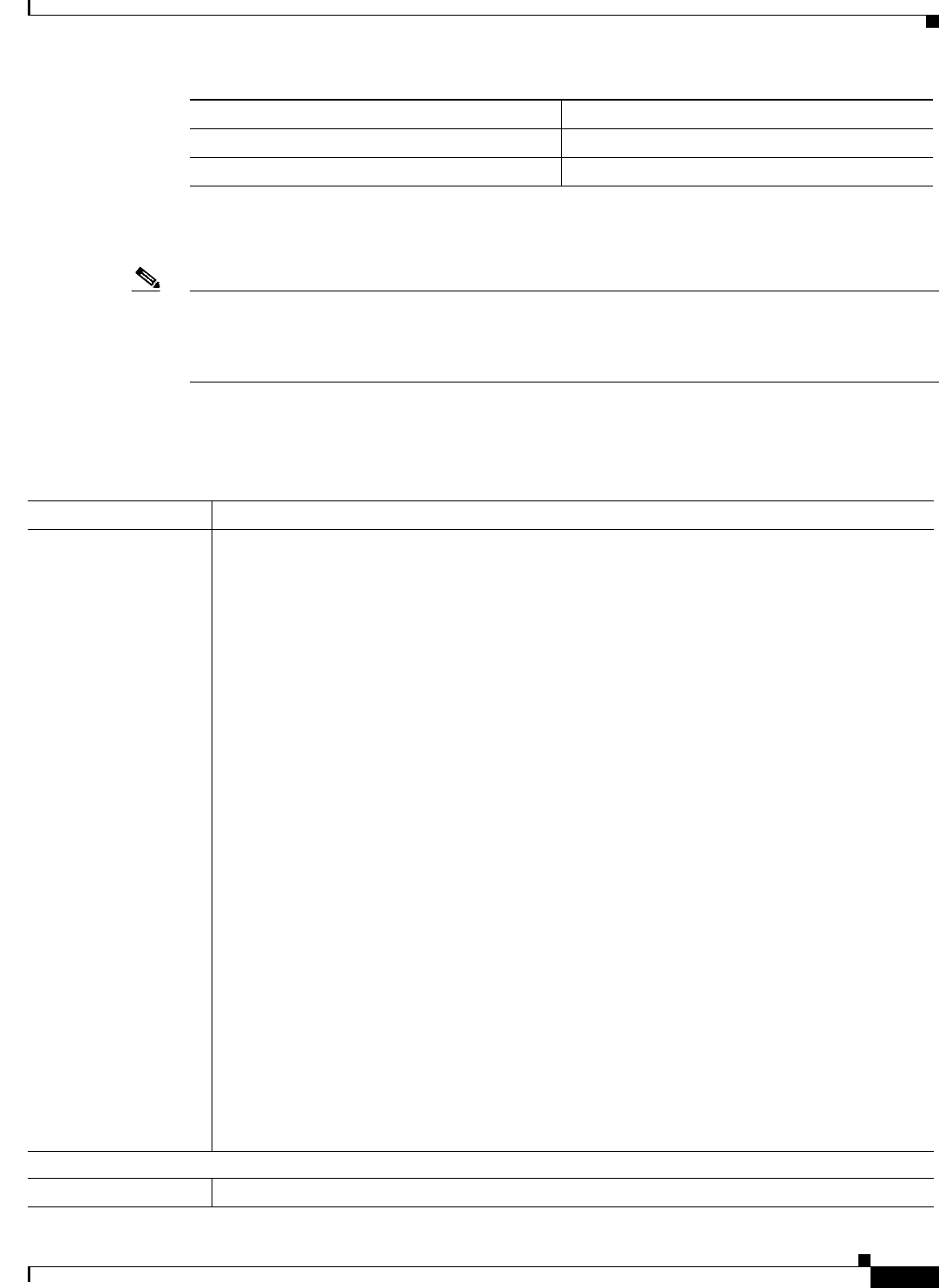
i.j.k.l 1
m.n.o.p 1
Device IP Failed Authentication Count
Table 12-11 Failed Authentications
Option Description
Failed Authentications Enter data according to the following:
greater than count > occurrences | %> in the past time> Minutes|Hours for a object, where:
• count values can be the absolute number of occurrences or percent. Valid values must be in the
range 0 to 99.
• occurrences | %> value can be occurrences or %.
• time values can be 1 to 1440 minutes, or 1 to 24 hours.
• Minutes|Hours value can be Minutes or Hours.
• object values can be:
–
ACS Instance
–
User
–
Identity Group
–
Device IP
–
Identity Store
–
Access Service
–
NAD Port
–
AuthZ Profile
–
AuthN Method
–
EAP AuthN
–
EAP Tunnel
In a distributed deployment, if there are two ACS instances, the count is calculated as an absolute
number or as a percentage for each of the instances. ACS triggers an alarm only when the individual
count of any of the ACS instance exceeds the specified threshold.
Filter
Failure Reason Click Select to enter a valid failure reason name on which to configure your threshold.


















