31-4
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 31 Managing Dynamic Access Policies for Remote Access VPNs (ASA 8.0+ Devices)
Configuring Dynamic Access Policies
DAP complements AAA services. It provides a limited set of authorization attributes that can override
those AAA provides. The security appliance selects DAP records based on the AAA authorization
information for the user and posture assessment information for the session. The security appliance can
select multiple DAP records depending on this information, which it then aggregates to create DAP
authorization attributes.
You can specify AAA attributes from the Cisco AAA attribute hierarchy, or from the full set of response
attributes that the security appliance receives from a RADIUS or LDAP server.
AAA Attribute Definitions
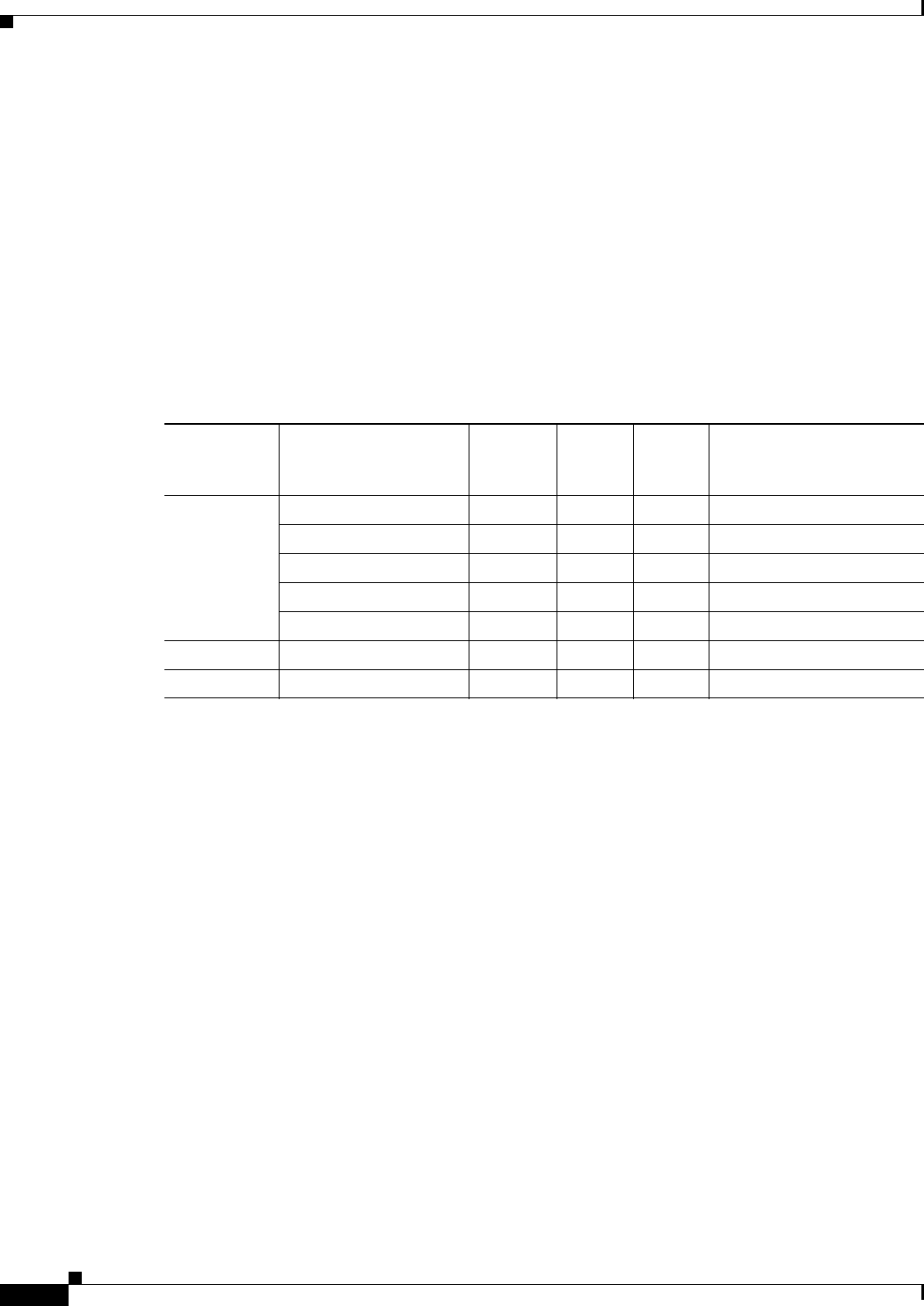
Table 31-1 on page 31-4 defines the AAA selection attribute names that are available for DAP use. The
Attribute Name field shows you how to enter each attribute name in a LUA logical expression, which
you might do on the Advanced tab of the Add/Edit Dynamic Access Policy dialog box.
DAP and Endpoint Security
The security appliance obtains endpoint security attributes by using posture assessment methods that you
configure. These include Cisco Secure Desktop and NAC. You can use a match of a prelogin policy,
Basic Host Scan entry, Host Scan Extension, or any combination of these and any other policy attributes
to assign access rights and restrictions. At minimum, configure DAPs to assign to each prelogin policy
and Basic Host Scan entry.
Endpoint Assessment, a Host Scan extension, examines the remote computer for a large collection of
antivirus and antispyware applications, associated definitions updates, and firewalls. You can use this
feature to combine endpoint criteria to satisfy your requirements before the security appliance assigns a
specific DAP to the session.
DAP and Anti-Virus, Anti-Spyware, and Personal Firewall Programs
The security appliance uses a DAP policy when the user attributes matches the configured AAA and
endpoint attributes. The Prelogin Assessment and Host Scan modules of Cisco Secure Desktop return
information to the security appliance about the configured endpoint attributes, and the DAP subsystem
uses that information to select a DAP record that matches the values of those attributes. Most, but not
all, anti-virus, anti-spyware, and personal firewall programs support active scan, which means that the
programs are memory-resident, and therefore always running. Host Scan checks to see if an endpoint has
a program installed, and if it is memory-resident as follows:
• If the installed program does not support active scan, Host Scan reports the presence of the software.
The DAP system selects DAP records that specify the program.
Table 31-1 AAA Attribute Definitions
Attribute Type Attribute Name Source Value
Max
String
Length Description
Cisco aaa.cisco.memberof AAA string 128 memberof value
aaa.cisco.username AAA string 64 username value
aaa.cisco.class AAA string 64 class attribute value
aaa.cisco.ipaddress AAA number – framed-ip address value
aaa.cisco.tunnelgroup AAA string 64 tunnel-group name
LDAP aaa.ldap.<label> LDAP string 128 LDAP attribute value pair
RADIUS aaa.radius.<number> RADIUS string 128 Radius attribute value pair


















