5-9
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 5 Managing Policies
Understanding Policies
Understanding Locking and Policies
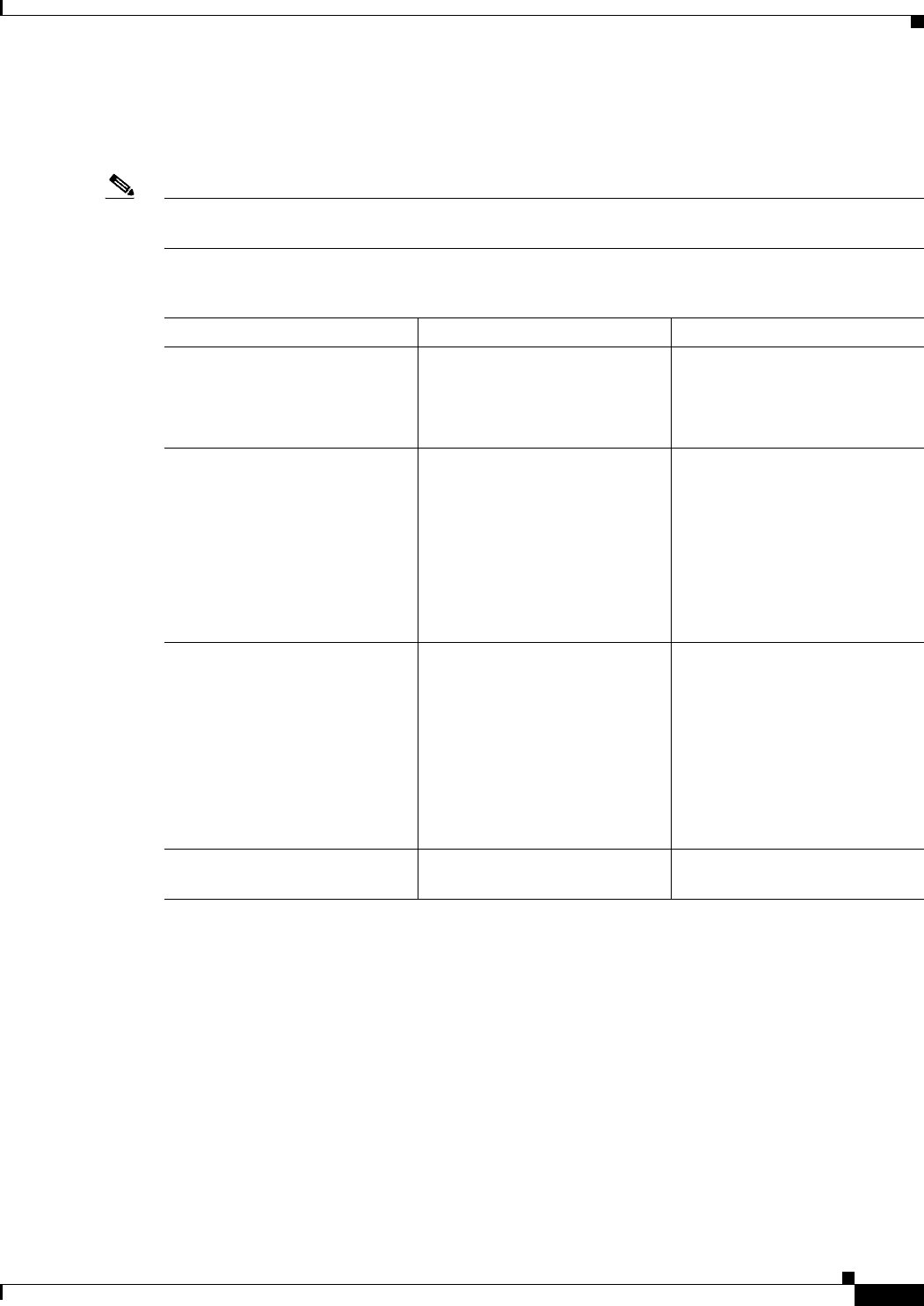
Table 5-1 on page 5-9 summarizes the effects of policy locks in Security Manager.
Note The ability to modify policies and policy assignments is dependent on the user permissions assigned to
the user. See the Installation Guide for Cisco Security Manager.
Related Topics
• Understanding Policy Locking, page 5-7
• Understanding Policies, page 5-1
Understanding Locking and VPN Topologies
If you change the device assignment for a VPN topology, or make changes to a specific VPN policy, a
lock is placed on the whole VPN topology, and on any other topologies in which the policy is shared.
This means that other users cannot make changes to the device assignment, nor can they make changes
to any of the VPN policies defined for those VPN topologies.
Table 5-1 Locking Summary
If Another User or Activity... You Cannot... You Can...
Changes a policy definition
• Modify the policy or assign
it to other devices.
• Unassign the policy (if it is a
local policy)
Unassign the policy from any
device (if it is shared).
Changes the definition of a
rule-based policy with
descendants
• Modify the parent policy or
any of the descendants.
• Assign the parent policy or
any of its descendants to
additional devices.
• Change the rule inheritance
of the parent policy or any of
the descendants.
Unassign the policy from any
device.
Changes a policy assignment
without changing its definition
Modify the policy.
Note In Policy view, a content
lock is placed on the
policy. In Device view,
an assignment lock is
placed on those devices
whose assignment is
being changed by the
other user.
Assign and unassign the policy
from other devices.
Changes a policy definition and
changes its assignment
Modify the policy or assign it to
other devices.
Unassign the policy from any
device.


















