63-9
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 63 Configuring Quality of Service
Quality of Service on Cisco IOS Routers
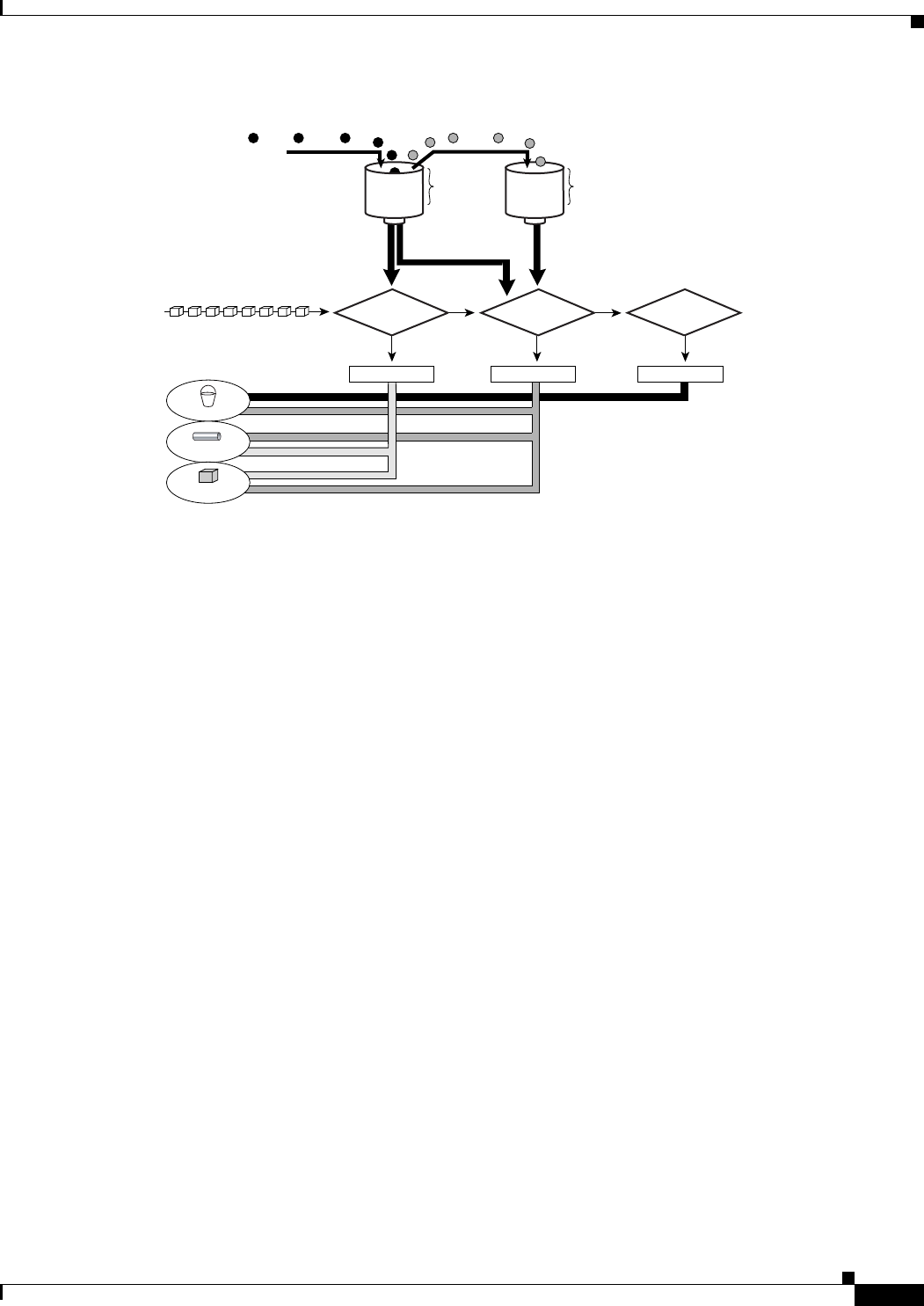
Figure 63-3 Two-Token Bucket Algorithm
When you use traffic policing, the token-bucket algorithm provides three actions for each packet: a
conform action, an exceed action, and an optional violate action. For instance, packets that conform can
be configured to be transmitted, packets that exceed can be configured to be sent with a decreased
priority, and packets that violate can be configured to be dropped.
Traffic policing is often configured on interfaces at the edge of a network to limit the rate of traffic
entering or leaving the network. In the most common traffic policing configurations, traffic that
conforms is transmitted and traffic that exceeds is sent with a decreased priority or is dropped. You can
change these configuration options to suit your network needs.
When you use traffic shaping, the token-bucket mechanism includes a data buffer for holding packets
that cannot be sent immediately. (Policers do not have such a buffer.) The token buckets permit packets
to be sent in bursts, but places bounds on this capability so that the flow is never faster than the capacity
of the buckets plus the time interval multiplied by the refill rate. The buffer also guarantees that the
long-term transmission rate does not exceed the CIR.
Related Topics
• Understanding Control Plane Policing, page 63-9
• Understanding Policing and Shaping Parameters, page 63-6
Understanding Control Plane Policing
The Control Plane Policing feature enables you to manage input traffic entering the control plane (CP)
of the router. The CP is a collection of processes that run at the process level on the route processor.
These processes collectively provide high-level control for most Cisco IOS functions. Control plane
policing protects the CP of Cisco IOS routers and switches against reconnaissance and denial-of-service
(DoS) attacks, enabling the CP to maintain packet forwarding and protocol states despite an attack or
heavy traffic load on the router or switch.
The Control Plane Policing feature treats the CP as a separate entity with its own ingress (input) and
egress (output) ports, enabling you to use Security Manager to configure QoS policies on input. These
policies are applied when a packet enters the CP. You can configure a QoS policy to prevent unwanted
SIZE < TC SIZE < Tc+ Te SIZE > Tc+ Te
yesyesyes
no
no
Bc Be
Tc: Tokens in bucket #1
Te: Tokens in bucket #2
Action
Drop
Transmit
Conform Exceed Violate
Remark Packet
144754


















