16-31
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 16 Managing Firewall Access Rules
Using Automatic Conflict Detection
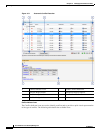
Conflict Details Area
The Conflict Details pane shows details for the selected conflict. The pane can be docked and undocked
as needed. If the Conflict Details pane is docked while the Policy Object Manager pane is also docked,
you can navigate between the two features using the tabs at the bottom of the window.
The conflicting rules are shown together in a table for easier direct comparison. The type of conflict is
shown above the table. A suggested action is shown below the table for all conflicts except partially
redundant rules and partially shadowed rules, which must be resolved manually. Links are provided for
direct navigation to the rules involved. Policy objects that are part of the conflicting rules can be
expanded by clicking on them to see the object contents. Click again to collapse the policy object.
You can use the links provided to navigate to the conflicting rules. You can also click the link under
Action to have Security Manager perform the suggested action automatically.
Conflict Navigation Buttons
The Previous Conflict and Next Conflict buttons at the top of the Conflict Details pane allow you to step
through the conflicts that need to be resolved without leaving the Conflict Details pane.
Related Topics
• Understanding Automatic Conflict Detection, page 16-25
• Resolving Conflicts, page 16-31
• Understanding Access Rules, page 16-1
• Understanding Device Specific Access Rule Behavior, page 16-4
• Understanding Access Rule Address Requirements and How Rules Are Deployed, page 16-5
• Configuring Access Rules, page 16-7
Resolving Conflicts
The following procedure explains how to use the Automatic Conflict Detection feature to resolve
conflicts in your access rules.
Tip You can use the Combine Rules tool to have Security Manager evaluate your rules and find ways to
combine them into more efficient rules. For more information, see Combining Rules, page 12-22.
Related Topics
• Understanding Automatic Conflict Detection, page 16-25
• Understanding the Automatic Conflict Detection User Interface, page 16-27
• Understanding Access Rules, page 16-1
• Understanding Device Specific Access Rule Behavior, page 16-4
• Understanding Access Rule Address Requirements and How Rules Are Deployed, page 16-5
• Configuring Access Rules, page 16-7
Step 1 Do one of the following:
• (Device view) Select Firewall > Access Rules from the Policy selector.