16-42
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 16 Managing Firewall Access Rules
Importing Rules
This example creates a network/host object named ftp_servers and two access rules.
Example 2: Restrict web access during working hours (ASA devices)
The following example denies HTTP requests between the hours of 8 AM and 6 PM, which are typical
work hours.
time-range no-http
periodic weekdays 8:00 to 18:00
access-list 101 deny tcp any any eq www time-range no-http
This example creates a time range object named no-http and one access rule.
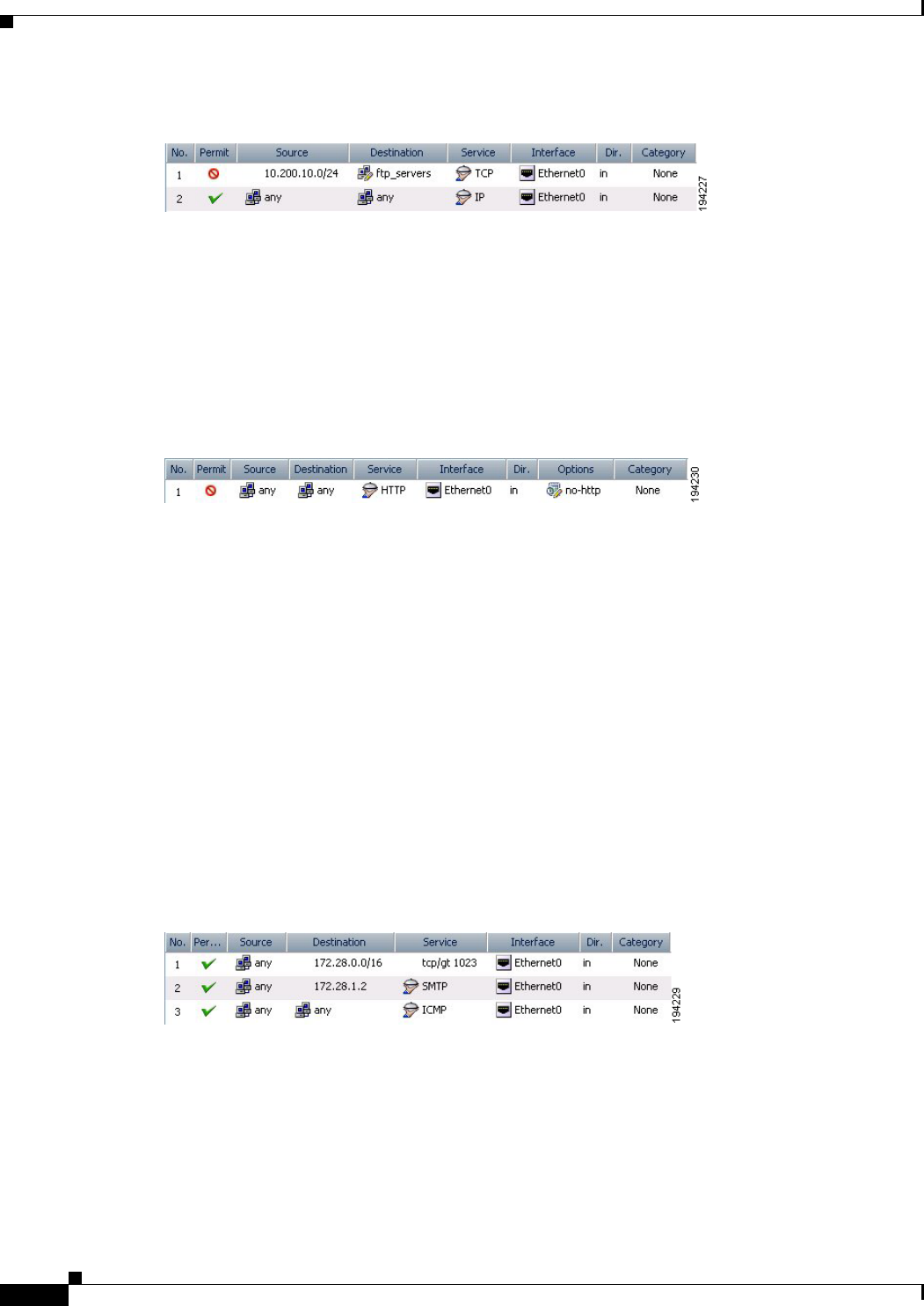
Example 3: Filtering on TCP and ICMP using port numbers (IOS devices)
In the following example, the first line of the extended access list named goodports permits any incoming
TCP connections with destination ports greater than 1023. The second line permits incoming TCP
connections to the Simple Mail Transfer Protocol (SMTP) port of host 172.28.1.2. The last line permits
incoming ICMP messages for error feedback.
ip access-list extended goodports
permit tcp any 172.28.0.0 0.0.255.255 gt 1023
permit tcp any host 172.28.1.2 eq 25
permit icmp any 172.28.0.0 255.255.255.255
This example creates three access rules. Notice that the wildcard masks used in the IOS ACL syntax are
converted to regular subnet masks. Security Manager automatically converts between standard
network/host subnet mask designations and the wildcard masks required in IOS ACLs. Because
ASA/PIX/FWSM requires the use of subnet masks in ACL commands, this makes it possible for you to
create rules that can apply to all devices; Security Manager takes care of converting your rules to the
correct syntax.
Example 4: Standard ACLs restricting hosts (IOS devices)
In the following example, the workstation belonging to Jones is allowed access to Ethernet interface 0
and the workstation belonging to Smith is not allowed access:
ip access-list standard workstations
remark Permit only Jones workstation through
permit 172.16.2.88


















