40-6
User Guide for Cisco Security Manager 4.4
OL-28826-01
Chapter 40 Managing IPS Anomaly Detection
Configuring Anomaly Detection
Configuring Anomaly Detection
Use the Anomaly Detection policy to configure anomaly detection settings. The Virtual Sensors policy
also contains a setting important for anomaly detection.
This procedure explains the overall configuration of anomaly detection. Before configuring these
settings, read the following topics:
• Understanding Anomaly Detection, page 40-1
• Worm Viruses, page 40-2
• Anomaly Detection Modes, page 40-2
• Anomaly Detection Zones, page 40-3
• Knowing When to Turn Off Anomaly Detection, page 40-4
• Configuring Anomaly Detection Signatures, page 40-4
Step 1 Do one of the following to open the Anomaly Detection policy you want to modify:
• (Device view) Select IPS > Anomaly Detection from the Policy selector.
• (Policy view) Select IPS > Anomaly Detection from the Policy selector. Select an existing policy
or create a new one.
The Anomaly detection policy includes these tabs:
• Operation Settings—Defines the worm timeout and identifies any IP addresses that should be
ignored by anomaly detection.
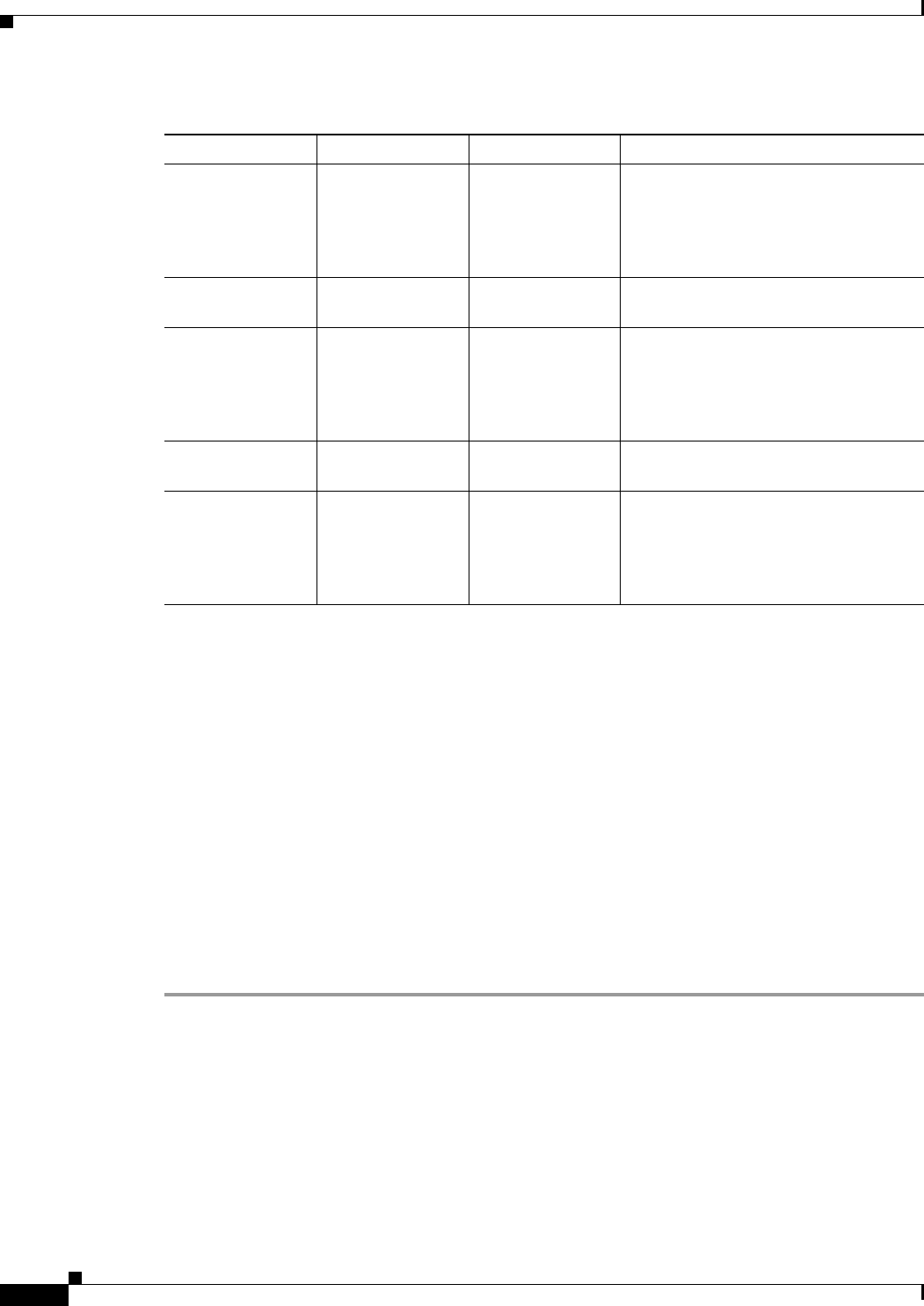
13006 1 Illegal TCP
Scanner
Identified a worm attack over a TCP
protocol in the illegal zone; the TCP
histogram threshold was crossed and a
scanner over a TCP protocol was
identified.
13007 0 Illegal UDP
Scanner
Identified a single scanner over a UDP
protocol in the illegal zone.
13007 1 Illegal UDP
Scanner
Identified a worm attack over a UDP
protocol in the illegal zone; the UDP
histogram threshold was crossed and a
scanner over a UDP protocol was
identified.
13008 0 Illegal Other
Scanner
Identified a single scanner over an
Other protocol in the illegal zone.
13008 1 Illegal Other
Scanner
Identified a worm attack over an Other
protocol in the illegal zone; the Other
histogram threshold was crossed and a
scanner over an Other protocol was
identified.
Table 40-1 Anomaly Detection Worm Signatures (Continued)
Signature ID Subsignature ID Name Description


















